Posted by Virus Bulletin on Apr 7, 2021
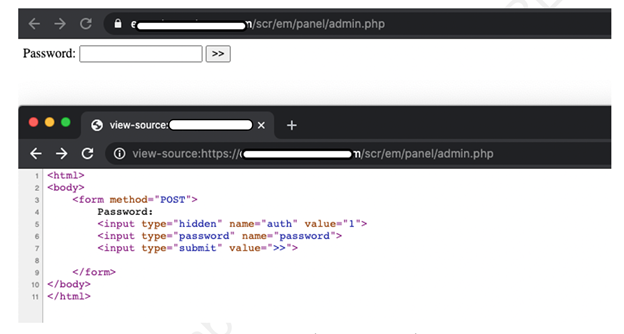 In a new article, Aditya K Sood looks at the command-and-control (C&C) design of the AZORult malware, discussing his team's findings related to the C&C design and some security issues they identified.
In a new article, Aditya K Sood looks at the command-and-control (C&C) design of the AZORult malware, discussing his team's findings related to the C&C design and some security issues they identified.
Posted by Virus Bulletin on Mar 17, 2021
 VB2021 localhost presents an exciting opportunity to share your research with an even wider cross section of the IT security community around the world than usual, without having to take time out of your work schedule (or budget) to travel.
VB2021 localhost presents an exciting opportunity to share your research with an even wider cross section of the IT security community around the world than usual, without having to take time out of your work schedule (or budget) to travel.
Posted by Virus Bulletin on Mar 2, 2021
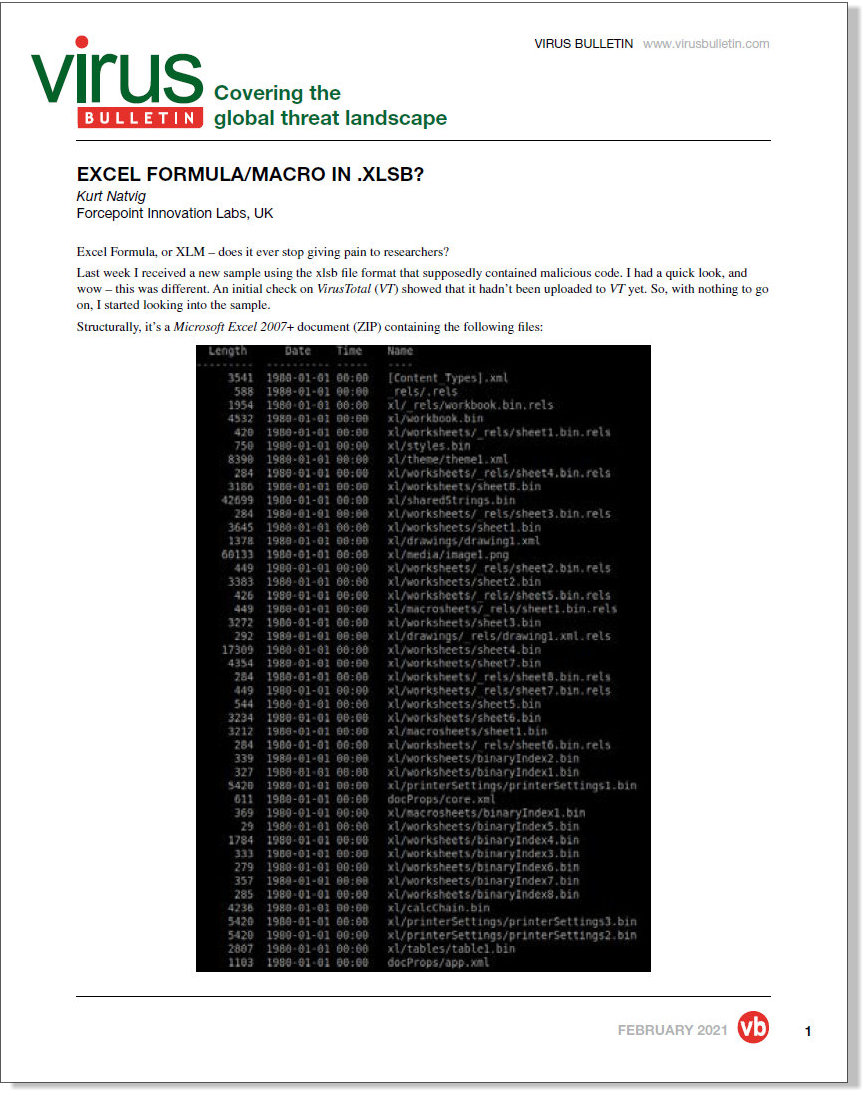 In a follow-up to an article published last week, Kurt Natvig takes us through the analysis of a new malicious sample using the .xlsb file format.
In a follow-up to an article published last week, Kurt Natvig takes us through the analysis of a new malicious sample using the .xlsb file format.
Posted by Virus Bulletin on Feb 23, 2021
 In a new article, researcher Kurt Natvig takes a close look at XF 4.0 malware.
In a new article, researcher Kurt Natvig takes a close look at XF 4.0 malware.
Posted by Virus Bulletin on Jan 29, 2021
 At VB2019, CSIS researcher Benoît Ancel spoke about a quiet banking trojan actor that has been targeting German users since at least 2014.
At VB2019, CSIS researcher Benoît Ancel spoke about a quiet banking trojan actor that has been targeting German users since at least 2014.
Posted by Virus Bulletin on Jan 19, 2021
 The call for papers for VB2021 is now open and we want to hear from you - we're planning for flexible presentation formats, so everyone is encouraged to submit, regardless of whether or not you know at this stage whether you'll be able to travel to Prague!
The call for papers for VB2021 is now open and we want to hear from you - we're planning for flexible presentation formats, so everyone is encouraged to submit, regardless of whether or not you know at this stage whether you'll be able to travel to Prague!
Posted by Virus Bulletin on Jan 11, 2021
 We were very sorry to learn of the passing of researcher Yonathan Klijnsma last week. Here, former VB Editor Martijn Grooten shares his memories of a talented researcher and a very kind person: this month, infosec lost a really good one.
We were very sorry to learn of the passing of researcher Yonathan Klijnsma last week. Here, former VB Editor Martijn Grooten shares his memories of a talented researcher and a very kind person: this month, infosec lost a really good one.
Posted by Virus Bulletin on Jan 8, 2021
 VB has made all VB2020 localhost presentations available on the VB YouTube channel, so you can now watch - and share - any part of the conference freely and without registration.
VB has made all VB2020 localhost presentations available on the VB YouTube channel, so you can now watch - and share - any part of the conference freely and without registration.
Posted by Virus Bulletin on Dec 8, 2020
 At VB2020 localhost, threat intelligence consultant Jamie Collier used the analytical technique of backcasting to look at the rise and fall of the cyber threat intelligence industry.
At VB2020 localhost, threat intelligence consultant Jamie Collier used the analytical technique of backcasting to look at the rise and fall of the cyber threat intelligence industry.
Posted by Virus Bulletin on Dec 4, 2020
 At VB2020 localhost, Carbon Black's Scott Knight presented an approach he and his colleagues have taken to more realistically simulate malware attacks.
At VB2020 localhost, Carbon Black's Scott Knight presented an approach he and his colleagues have taken to more realistically simulate malware attacks.