Posted by Martijn Grooten on Sep 4, 2017
 A security researcher found more than 700 million email addresses stored on a server used by a spam botnet, which gives us some insight into what the email lists used by spammers look like.
A security researcher found more than 700 million email addresses stored on a server used by a spam botnet, which gives us some insight into what the email lists used by spammers look like.
Posted by Martijn Grooten on Sep 4, 2017
 We preview the VB2017 presentation by Tyrus Kamau (Euclid Security), who will talk about the state of cybersecurity in Africa, with a particular focus on his home country, Kenya.
We preview the VB2017 presentation by Tyrus Kamau (Euclid Security), who will talk about the state of cybersecurity in Africa, with a particular focus on his home country, Kenya.
Posted by Martijn Grooten on Aug 31, 2017
 We preview the VB2017 Small Talk to be given by AppEsteem's Dennis Batchelder that should help security vendors make decisions about apps whose behaviours sit right on the limits of what is acceptable from a security point of view.
We preview the VB2017 Small Talk to be given by AppEsteem's Dennis Batchelder that should help security vendors make decisions about apps whose behaviours sit right on the limits of what is acceptable from a security point of view.
Posted by Martijn Grooten on Aug 30, 2017
We preview the VB2017 paper by Forcepoint's Kristin Leary and Richard Ford, who will discuss a practical approach to preventing insider attacks.
Read morePosted by Martijn Grooten on Aug 29, 2017
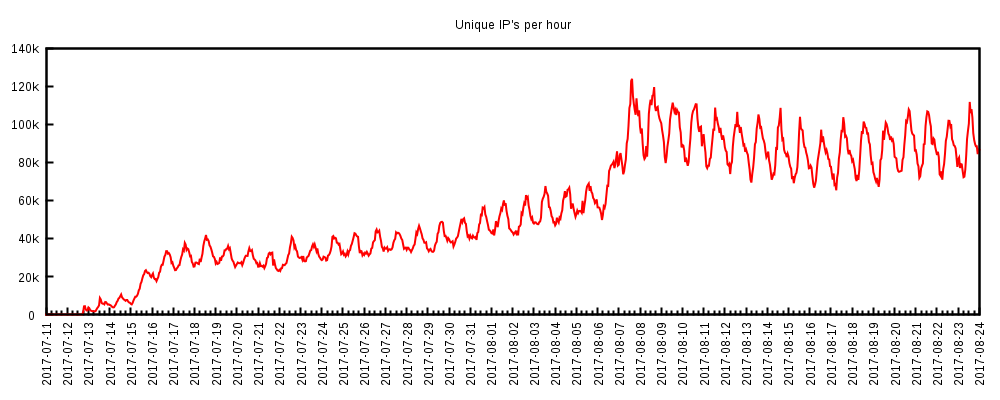 Collaboration between a number of security companies has led to the takedown of the WireX Android DDoS botnet. Efforts like these, and the fact that the companies involved all decided to publish the very same blog post, show the best side of the security industry.
Collaboration between a number of security companies has led to the takedown of the WireX Android DDoS botnet. Efforts like these, and the fact that the companies involved all decided to publish the very same blog post, show the best side of the security industry.
Posted by Martijn Grooten on Aug 28, 2017
We preview the VB2017 presentation by Mick Moran, who will discuss online child abuse and the role the security community can play fighting it.
Read morePosted by Martijn Grooten on Aug 28, 2017
Researchers at Mimecast have published a paper about the 'ROPEMAKER' exploit, which allows an email sender with malicious intentions to change the visial appearance of an email after it has been delivered.
Read morePosted by Martijn Grooten on Aug 25, 2017
 We preview the VB2017 presentation by Kaspersky Lab researchers Thiago Marques and Fabio Assolini in which they look at malware targeting ATMs in Latin America.
We preview the VB2017 presentation by Kaspersky Lab researchers Thiago Marques and Fabio Assolini in which they look at malware targeting ATMs in Latin America.
Posted by Martijn Grooten on Aug 24, 2017
 We preview the VB2017 paper by Microsoft's Holly Stewart and Joe Blackbird, which uses data about users switching anti-virus provider to decide whether machine-learning models should favour avoiding false positives over false negatives.
We preview the VB2017 paper by Microsoft's Holly Stewart and Joe Blackbird, which uses data about users switching anti-virus provider to decide whether machine-learning models should favour avoiding false positives over false negatives.
Posted by Martijn Grooten on Aug 23, 2017
 We preview the VB2017 presentation by Jelena Milosevic, an ICU nurse by profession, who will provide the audience with an inside view of security in hospitals.
We preview the VB2017 presentation by Jelena Milosevic, an ICU nurse by profession, who will provide the audience with an inside view of security in hospitals.