Posted by Martijn Grooten on Mar 8, 2017
 Is it your job to defend your company’s network? Are you defending a government’s systems? Do you help secure the devices used by activists operating in less open societies? Do you work with abuse victims targeted by spyware? Share your experiences with the security community at VB2017.
Is it your job to defend your company’s network? Are you defending a government’s systems? Do you help secure the devices used by activists operating in less open societies? Do you work with abuse victims targeted by spyware? Share your experiences with the security community at VB2017.
Posted by Virus Bulletin on Mar 8, 2017
At Virus Bulletin, we love the BSides concept and we have attended several of the BSides events around the world. So when Peter Karsai, who is soon to join the VB team, offered to write about his experience at BSides Budapest, we jumped at the chance to publish his post.
Read morePosted by Martijn Grooten on Mar 6, 2017
 We are excited to announce the first five sponsors of VB2017, companies based in Europe, Asia and North America.
We are excited to announce the first five sponsors of VB2017, companies based in Europe, Asia and North America.
Posted by Martijn Grooten on Feb 27, 2017
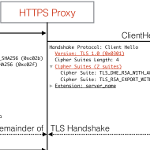 A recent paper showed that many HTTPS-intercepting security solutions have implemented TLS rather poorly. Does that mean we should avoid such solutions altogether?
A recent paper showed that many HTTPS-intercepting security solutions have implemented TLS rather poorly. Does that mean we should avoid such solutions altogether?
Posted by Martijn Grooten on Feb 23, 2017
 Researchers from Google and CWI Amsterdam have created the first known collision of the SHA-1 hashing algorithm, making a very strong case to ditch it.
Researchers from Google and CWI Amsterdam have created the first known collision of the SHA-1 hashing algorithm, making a very strong case to ditch it.
Posted by Helen Martin on Feb 23, 2017
 VB was saddened to learn this week of the passing of one of the pioneers of the AV industry, Ross Greenberg. This Throwback Thursday we look back at an interview with Ross in November 1995.
VB was saddened to learn this week of the passing of one of the pioneers of the AV industry, Ross Greenberg. This Throwback Thursday we look back at an interview with Ross in November 1995.
Posted by Martijn Grooten on Feb 20, 2017
 Have you analysed a new online threat? Do you know a new way to defend against such threats? Then submit an abstract in the CFP for VB2017!
Have you analysed a new online threat? Do you know a new way to defend against such threats? Then submit an abstract in the CFP for VB2017!
Posted by Martijn Grooten on Feb 17, 2017
APT reports are great for gaining an understanding of how advanced attack groups operate - however, they can also provide free QA for the threat actors. Today, we publish a VB2016 paper by Gadi Evron (Cymmetria) and Inbar Raz (Perimeter X), who discuss what they think is wrong with many APT reports and what can be done to improve them.
Read morePosted by Martijn Grooten on Feb 14, 2017
Industry veteran Mikko Hyppönen recently urged would-be security researchers to ditch their favourite pop music and listen to security podcasts on their commute to work instead. Virus Bulletin Editor Martijn Grooten shares his favourite security podcasts.
Read morePosted by Martijn Grooten on Feb 10, 2017
In a presentation at VB2016, Patrick Wardle, Director of Research at Synack, discussed the possibilities of Mac malware recording the user via the webcam. Today, we publish the video of Patrick's presentation.
Read more