Posted by Martijn Grooten on Apr 18, 2018
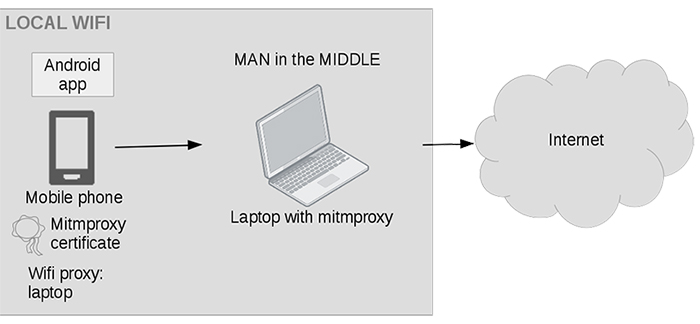 Within a few years, Android malware has grown from a relatively small threat to a huge problem involving more than three million new malware samples a year. Axelle Apvrille, one of the world's leading Android malware researchers, will deliver a workshop on Android reverse engineering at VB2018 in Montreal this October. Last year, Axelle presented a paper at VB2017 on some of the less common tools that can be used to reverse engineer Android malware. Today, we publish both the paper and the recording of Axelle's presentation.
Within a few years, Android malware has grown from a relatively small threat to a huge problem involving more than three million new malware samples a year. Axelle Apvrille, one of the world's leading Android malware researchers, will deliver a workshop on Android reverse engineering at VB2018 in Montreal this October. Last year, Axelle presented a paper at VB2017 on some of the less common tools that can be used to reverse engineer Android malware. Today, we publish both the paper and the recording of Axelle's presentation.
Posted by Martijn Grooten on Apr 16, 2018
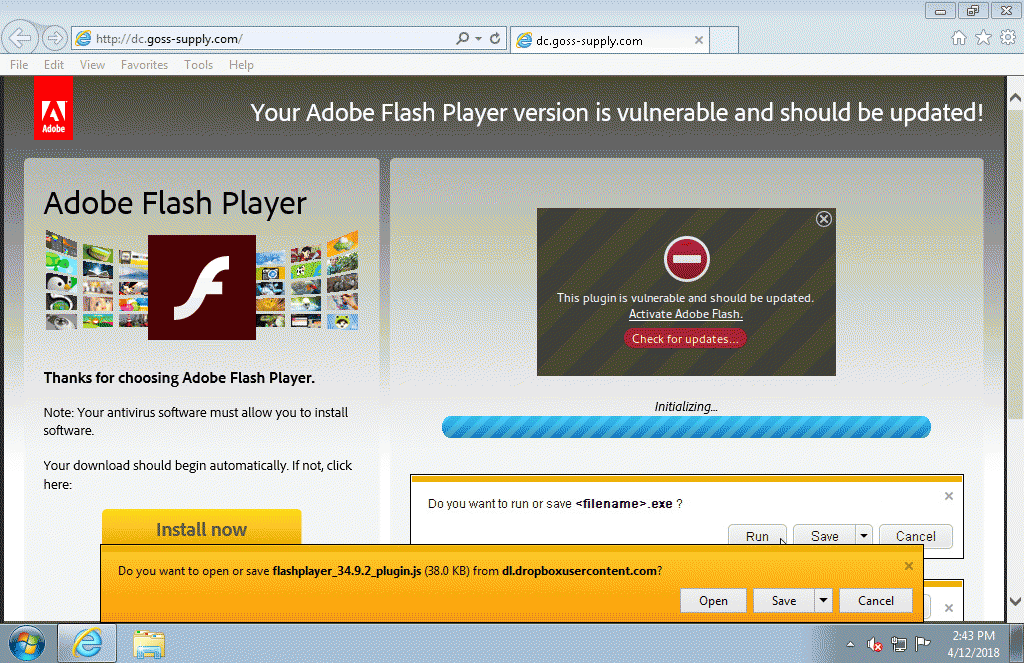 Compromised websites are being used to serve fake Flash Player uploads that come with a malicious payload.
Compromised websites are being used to serve fake Flash Player uploads that come with a malicious payload.
Posted by Martijn Grooten on Apr 13, 2018
 Next week, VB Editor Martijn Grooten will be at the RSA Conference in San Francisco.
Next week, VB Editor Martijn Grooten will be at the RSA Conference in San Francisco.
Posted by Martijn Grooten on Apr 11, 2018
 VB is excited to reveal the details of an interesting and diverse programme for VB2018, the 28th Virus Bulletin International Conference, which takes place 3-5 October in Montreal, Canada.
VB is excited to reveal the details of an interesting and diverse programme for VB2018, the 28th Virus Bulletin International Conference, which takes place 3-5 October in Montreal, Canada.
Posted by Martijn Grooten on Apr 10, 2018
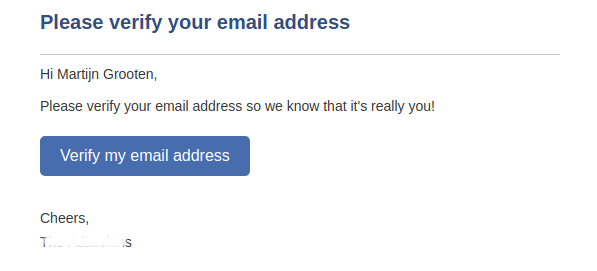 A clever trick taking advantage of the fact that Gmail ignores dots in email addresses could be used to trick someone into paying for your Netflix subscription - demonstrating the importance of confirmed opt-in.
A clever trick taking advantage of the fact that Gmail ignores dots in email addresses could be used to trick someone into paying for your Netflix subscription - demonstrating the importance of confirmed opt-in.
Posted by Martijn Grooten on Apr 10, 2018
 At VB2017 in Madrid, Malwarebytes' Chris Boyd presented a paper in which he looked at various aspects of advergaming, from unreadable EULAs to fake programs that promise to block ads. Today, we publish both the paper and the recording of Chris's presentation.
At VB2017 in Madrid, Malwarebytes' Chris Boyd presented a paper in which he looked at various aspects of advergaming, from unreadable EULAs to fake programs that promise to block ads. Today, we publish both the paper and the recording of Chris's presentation.
Posted by Martijn Grooten on Mar 27, 2018
 Two or more mobile apps, viewed independently, may not appear to be malicious - but in combination, they could become harmful by exchanging information with one another and by performing malicious activities together. Today, we publish a new paper by a group of researchers affiliated with various UK universities and companies, which looks at how machine-learning methods can be used to detect app collusions.
Two or more mobile apps, viewed independently, may not appear to be malicious - but in combination, they could become harmful by exchanging information with one another and by performing malicious activities together. Today, we publish a new paper by a group of researchers affiliated with various UK universities and companies, which looks at how machine-learning methods can be used to detect app collusions.
Posted by Martijn Grooten on Mar 26, 2018
 At VB2016 in Denver, Jorge Blasco presented a paper (co-written with Thomas M. Chen, Igor Muttik and Markus Roggenbach), in which he discussed the concept of app collusion - where two (or more) apps installed on the same device work together to collect and extract data from the device - and presented discoveries of colluding code in many in-the-wild apps. Today, we publish both the paper and the recording of Jorge's presentation.
At VB2016 in Denver, Jorge Blasco presented a paper (co-written with Thomas M. Chen, Igor Muttik and Markus Roggenbach), in which he discussed the concept of app collusion - where two (or more) apps installed on the same device work together to collect and extract data from the device - and presented discoveries of colluding code in many in-the-wild apps. Today, we publish both the paper and the recording of Jorge's presentation.
Posted by Martijn Grooten on Mar 19, 2018
 At VB2017 in Madrid, Polish security researcher and journalist Adam Haertlé presented a paper about a very inept persistent threat. Today, we publish both the paper and the recording of Adam's presentation.
At VB2017 in Madrid, Polish security researcher and journalist Adam Haertlé presented a paper about a very inept persistent threat. Today, we publish both the paper and the recording of Adam's presentation.
Posted by Martijn Grooten on Mar 16, 2018
 The call for papers for VB2018 closes on 18 March, and while we've already received many great submissions, we still want more! Here are five reasons why you should submit a paper this weekend.
The call for papers for VB2018 closes on 18 March, and while we've already received many great submissions, we still want more! Here are five reasons why you should submit a paper this weekend.