Posted by Virus Bulletin on Oct 6, 2020
 VB2020 localhost - VB's first foray into the world of virtual conferences - took place last week, but you can still watch all the presentations.
VB2020 localhost - VB's first foray into the world of virtual conferences - took place last week, but you can still watch all the presentations.
Posted by Virus Bulletin on Aug 25, 2020
 The programme for VB2020 localhost - the first virtual, and entirely free to attend VB conference - is now complete, with new additions to both the live programme and the on-demand programme.
The programme for VB2020 localhost - the first virtual, and entirely free to attend VB conference - is now complete, with new additions to both the live programme and the on-demand programme.
Posted by Virus Bulletin on Aug 10, 2020
 Why VB2020 localhost presents a unique opportunity for you to share your research with security experts around the globe.
Why VB2020 localhost presents a unique opportunity for you to share your research with security experts around the globe.
Posted by Virus Bulletin on Jul 31, 2020
 The call for last-minute papers for VB2020 localhost is now open. Submit before 17 August to have your paper considered for one of the nine slots reserved for 'hot' research!
The call for last-minute papers for VB2020 localhost is now open. Submit before 17 August to have your paper considered for one of the nine slots reserved for 'hot' research!
Posted by Virus Bulletin on Jul 29, 2020
 Announcing VB2020 localhost: the carbon neutral, budget neutral VB conference!
Announcing VB2020 localhost: the carbon neutral, budget neutral VB conference!
Posted by Virus Bulletin on May 4, 2020
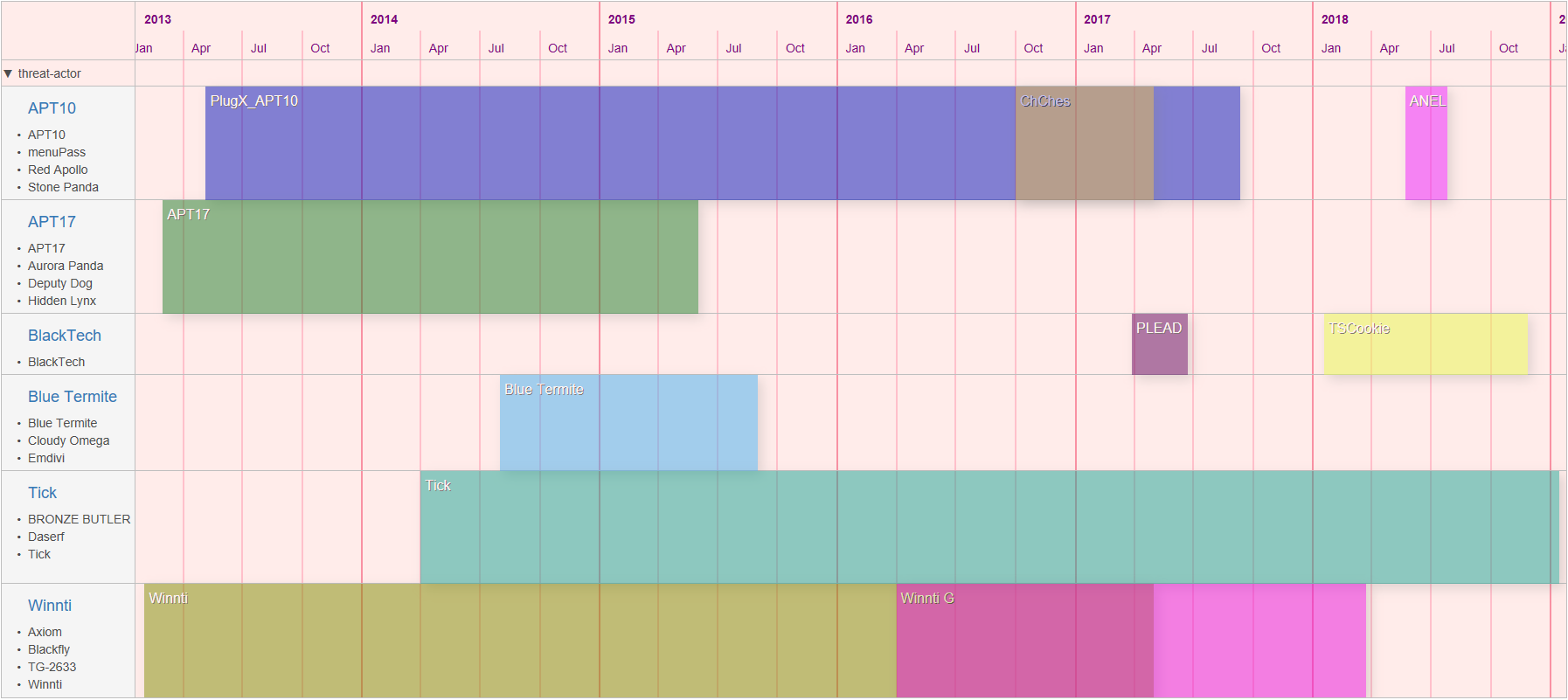 At VB2019, JPCERT/CC's Shusei Tomonaga and Tomoaki Tani presented a paper on attacks that exploit vulnerabilities in software used only in Japan, using malware that is unique to Japan. Today we publish both their paper and the recording of their presentation.
At VB2019, JPCERT/CC's Shusei Tomonaga and Tomoaki Tani presented a paper on attacks that exploit vulnerabilities in software used only in Japan, using malware that is unique to Japan. Today we publish both their paper and the recording of their presentation.
Posted by Helen Martin on Apr 30, 2020
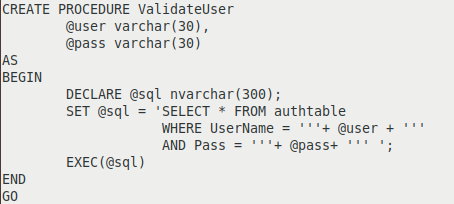 In a follow-up to a paper presented at VB2019, Prismo Systems researchers Abhishek Singh and Ramesh Mani detail algorithms that can be used to detect SQL injection in stored procedures, persistent cross-site scripting (XSS), and server‑side request forgery (SSRF) by instrumenting web applications.
In a follow-up to a paper presented at VB2019, Prismo Systems researchers Abhishek Singh and Ramesh Mani detail algorithms that can be used to detect SQL injection in stored procedures, persistent cross-site scripting (XSS), and server‑side request forgery (SSRF) by instrumenting web applications.
Posted by Virus Bulletin on Apr 16, 2020
 VB is pleased to reveal the details of an interesting and diverse programme for VB2020, the 30th Virus Bulletin International Conference.
VB is pleased to reveal the details of an interesting and diverse programme for VB2020, the 30th Virus Bulletin International Conference.
Posted by Virus Bulletin on Apr 2, 2020
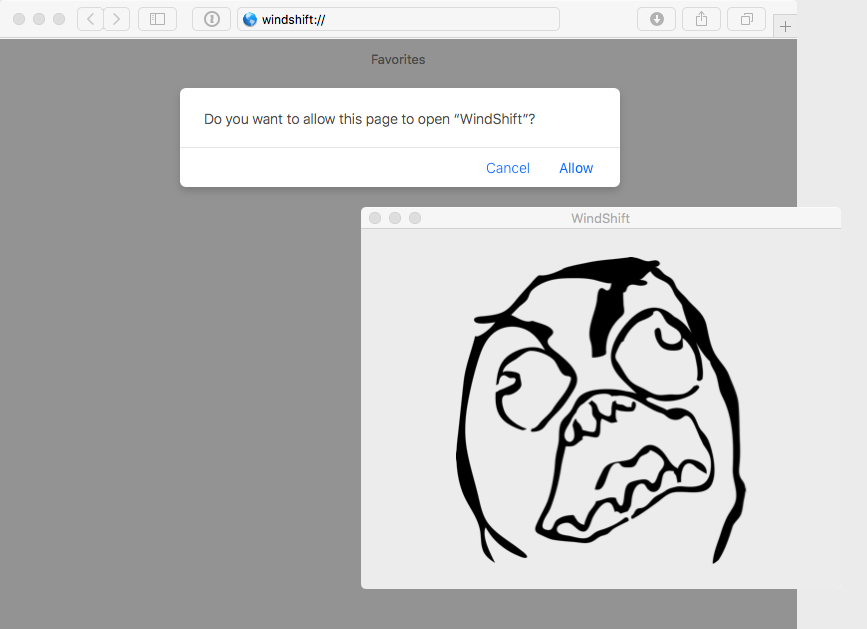 At VB2019 in London, Jamf's Patrick Wardle analysed the WindTail macOS malware used by the WindShift APT group, active in the Middle East. Today we publish both Patrick's paper and the recording of his presentation.
At VB2019 in London, Jamf's Patrick Wardle analysed the WindTail macOS malware used by the WindShift APT group, active in the Middle East. Today we publish both Patrick's paper and the recording of his presentation.
Posted by Virus Bulletin on Mar 24, 2020
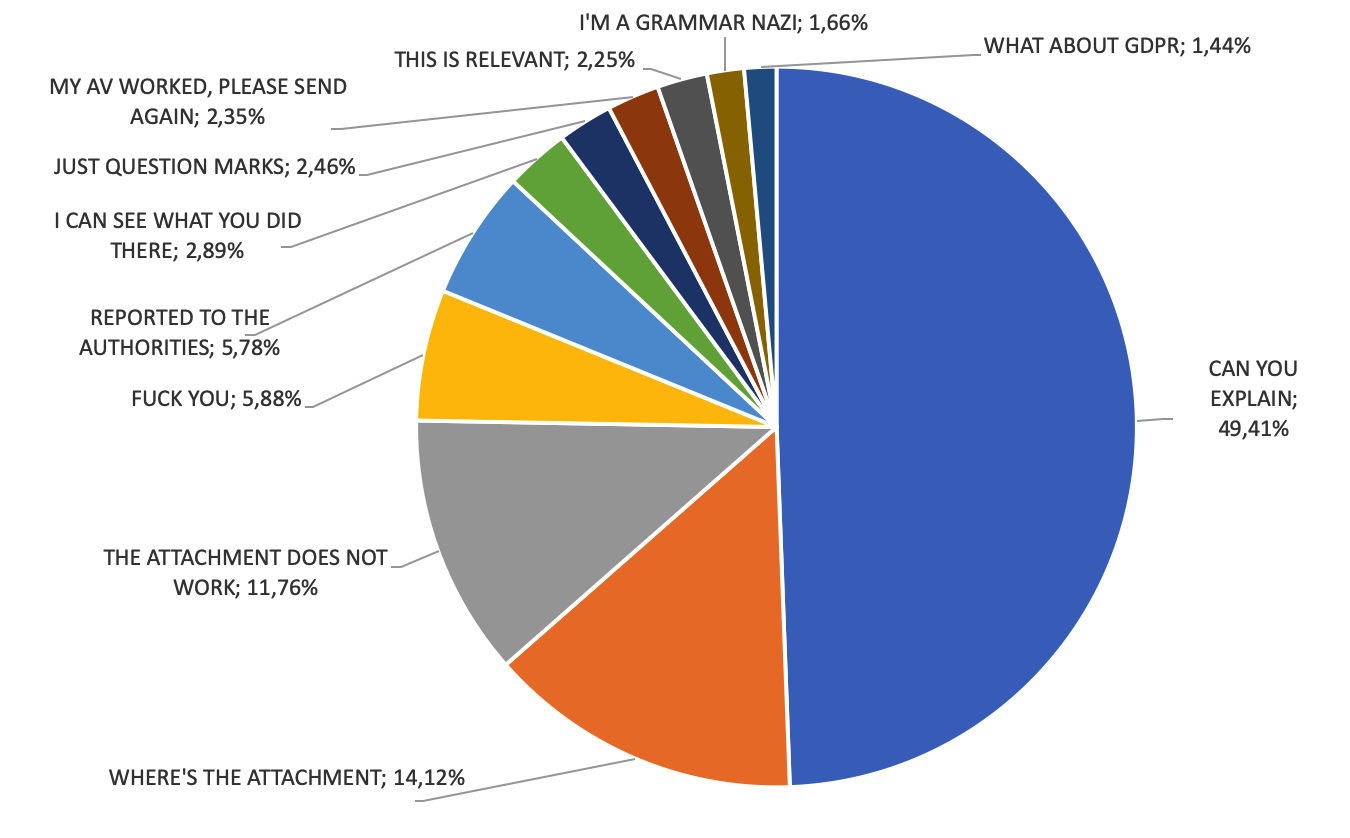 At VB2019 cybercrime journalist and researcher Adam Haertlé presented an analysis of almost 2000 unsolicited responses sent by victims of a malicious email campaign. Today we publish both his paper and the recording of his presentation.
At VB2019 cybercrime journalist and researcher Adam Haertlé presented an analysis of almost 2000 unsolicited responses sent by victims of a malicious email campaign. Today we publish both his paper and the recording of his presentation.