Posted by Martijn Grooten on Nov 29, 2016
While the Internet of Things blossoms with newly connected objects every day, the security and privacy of these objects is often overlooked, making the IoT a major security concern. Unfortunately, reverse-engineering so-called smart devices is not an easy task. In her VB2016 paper, Axelle Apvrille presented a novel way of analysing smart devices: by looking at the accompanying mobile app. Today, we publish both Axelle’s paper and the video recording of her VB2016 presentation.
Read morePosted by Martijn Grooten on Nov 21, 2016
Today, we publish the VB2016 paper and presentation (recording) by Kaspersky Lab researchers Juan Andrés Guerrero-Saade and Brian Bartholomew, in which they look at some of the deception tactics used in targeted attacks.
Read morePosted by Helen Martin on Nov 10, 2016
 President-elect of the United States Donald Trump made a number of promises about cybersecurity during his electoral campaign. What comes of those pledges remains to be seen, but one thing is certain: there will be a team of hard-working, dedicated individuals working behind the scenes to protect the computer systems of Federal government agencies, as there have been for years. Back in 1999, VB published a report describing a day in the life of the Affiliated Computer Services Government Solutions Group (ACS GSG) - the group responsible for providing full service computer support to US Federal government agencies across the United States.
President-elect of the United States Donald Trump made a number of promises about cybersecurity during his electoral campaign. What comes of those pledges remains to be seen, but one thing is certain: there will be a team of hard-working, dedicated individuals working behind the scenes to protect the computer systems of Federal government agencies, as there have been for years. Back in 1999, VB published a report describing a day in the life of the Affiliated Computer Services Government Solutions Group (ACS GSG) - the group responsible for providing full service computer support to US Federal government agencies across the United States.
Posted by Martijn Grooten on Oct 18, 2016
 We publish Aditya K. Sood's VB2016 paper on the use of iframe injectors by cybercriminals to deliver drive-by downloads.
We publish Aditya K. Sood's VB2016 paper on the use of iframe injectors by cybercriminals to deliver drive-by downloads.
Posted by Virus Bulletin on Sep 26, 2016
 An interview with VB2016’s keynote speaker Christine Whalley - Director, Governance and IT Risk Management at Pfizer
An interview with VB2016’s keynote speaker Christine Whalley - Director, Governance and IT Risk Management at Pfizer
Posted by Helen Martin on Sep 22, 2016
 In 1999, Christine Orshesky described how one large organization decided to find out how and where the viruses within it were being obtained so it could do more to protect its networks.
In 1999, Christine Orshesky described how one large organization decided to find out how and where the viruses within it were being obtained so it could do more to protect its networks.
Posted by Martijn Grooten on Sep 15, 2016
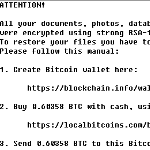 At VB2016, two talks will discuss mistakes made by malware authors in cryptographic implementations. Ben Herzog and Yaniv Balmas will present a paper in which they look at a number of these mistakes, while Malwarebytes researcher hasherezade will present a last-minute paper on making use of some of these mistakes to crack ransomware.
At VB2016, two talks will discuss mistakes made by malware authors in cryptographic implementations. Ben Herzog and Yaniv Balmas will present a paper in which they look at a number of these mistakes, while Malwarebytes researcher hasherezade will present a last-minute paper on making use of some of these mistakes to crack ransomware.
Posted by Virus Bulletin on Sep 14, 2016
Next month at VB2016, HPE Security's Oleg Petrovsky will speak about attacks on GPS. We conducted a short interview with Oleg and asked him about GPS, about the conference, and about his ultimate dinner party.
Read morePosted by Martijn Grooten on Sep 13, 2016
 If you are coming to VB2016 in Denver, why not spend an extra day in the Mile-High City and join the free BSides Denver conference, which takes place on Saturday?
If you are coming to VB2016 in Denver, why not spend an extra day in the Mile-High City and join the free BSides Denver conference, which takes place on Saturday?
Posted by Martijn Grooten on Sep 13, 2016
 We are excited to announce the addition of the "last-minute" papers to the VB2016 programme: nine presentations covering hot research topics, from OS X attacks to exotic APTs, breaking ransomware and the current state of BGP.
We are excited to announce the addition of the "last-minute" papers to the VB2016 programme: nine presentations covering hot research topics, from OS X attacks to exotic APTs, breaking ransomware and the current state of BGP.