Posted by Martijn Grooten on Jan 15, 2019
 Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2019 is now open and we want to hear from you!
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2019 is now open and we want to hear from you!
Posted by Martijn Grooten on Jan 14, 2019
 Today, we publish a VB2018 paper by Google researcher Maddie Stone in which she looks at one of the most interesting anti-analysis native libraries in the Android ecosystem. We also release the recording of Maddie's presentation.
Today, we publish a VB2018 paper by Google researcher Maddie Stone in which she looks at one of the most interesting anti-analysis native libraries in the Android ecosystem. We also release the recording of Maddie's presentation.
Posted by Martijn Grooten on Jan 7, 2019
 Today, we publish the VB2018 paper by Chronicle researcher Juan Andres Guerrero-Saade, who argues we should change the way we talk about APT actors.
Today, we publish the VB2018 paper by Chronicle researcher Juan Andres Guerrero-Saade, who argues we should change the way we talk about APT actors.
Posted by Martijn Grooten on Dec 19, 2018
 VB Editor Martijn Grooten reviews Charles Arthur's Cyber Wars, which looks at seven prominent hacks and attacks, and the lessons we can learn from them.
VB Editor Martijn Grooten reviews Charles Arthur's Cyber Wars, which looks at seven prominent hacks and attacks, and the lessons we can learn from them.
Posted by Martijn Grooten on Dec 14, 2018
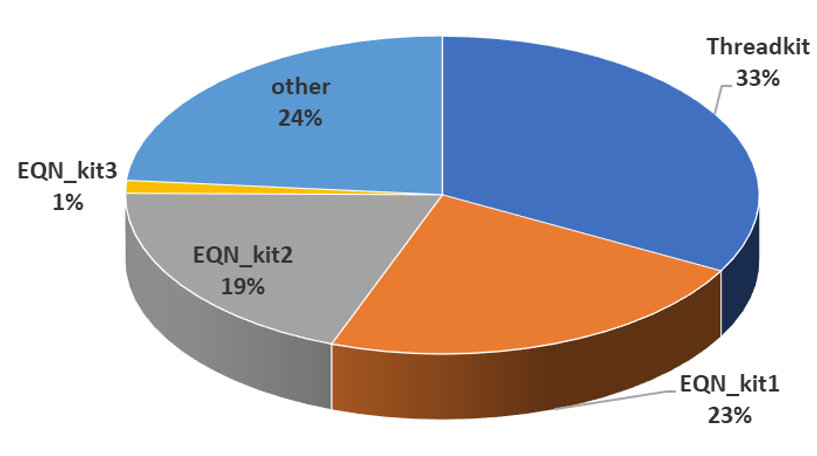 At VB2018 Sophos researcher Gábor Szappanos provided a detailed overview of Office exploit builders, and looked in particular at the widely exploited CVE-2017-0199. Today we publish his paper and release the video of his presentation.
At VB2018 Sophos researcher Gábor Szappanos provided a detailed overview of Office exploit builders, and looked in particular at the widely exploited CVE-2017-0199. Today we publish his paper and release the video of his presentation.
Posted by Martijn Grooten on Dec 12, 2018
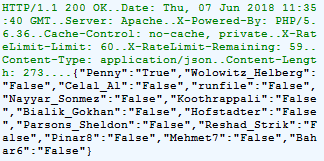 Today, we release the video of the VB2018 presentation by Check Point researcher Aseel Kayal, who connected the various dots relating to campaigns by the APT-C-23 threat group.
Today, we release the video of the VB2018 presentation by Check Point researcher Aseel Kayal, who connected the various dots relating to campaigns by the APT-C-23 threat group.
Posted by Martijn Grooten on Dec 11, 2018
 VB calls on organisations and individuals involved in threat intelligence from around the world to participate in next year's Virus Bulletin conference.
VB calls on organisations and individuals involved in threat intelligence from around the world to participate in next year's Virus Bulletin conference.
Posted by Martijn Grooten on Dec 7, 2018
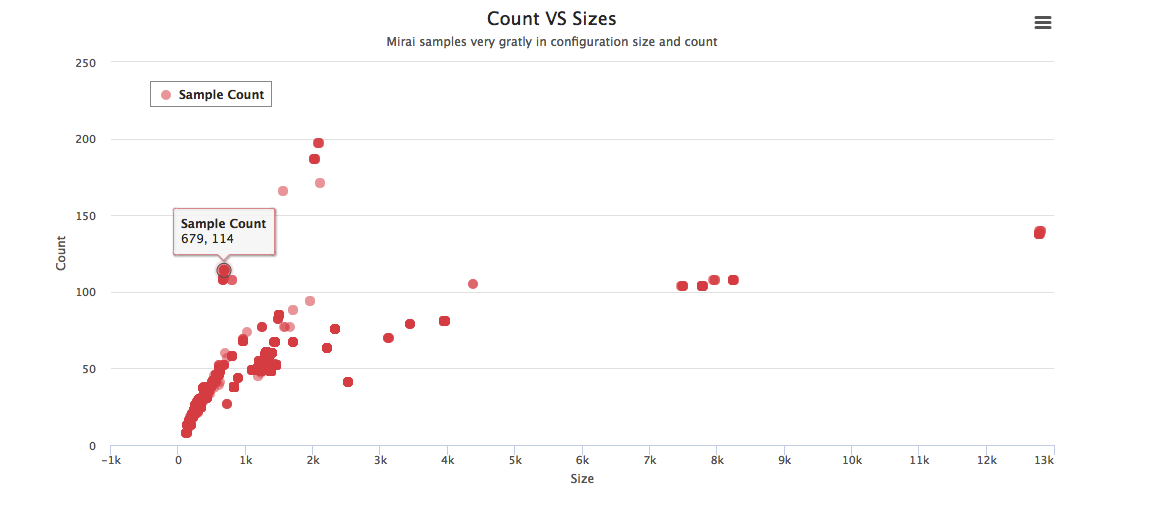 Today, we publish the VB2018 paper by Qihoo 360 researchers Ya Liu and Hui Wang, on extracting data from variants of the Mirai botnet to classify and track variants.
Today, we publish the VB2018 paper by Qihoo 360 researchers Ya Liu and Hui Wang, on extracting data from variants of the Mirai botnet to classify and track variants.
Posted by Martijn Grooten on Dec 6, 2018
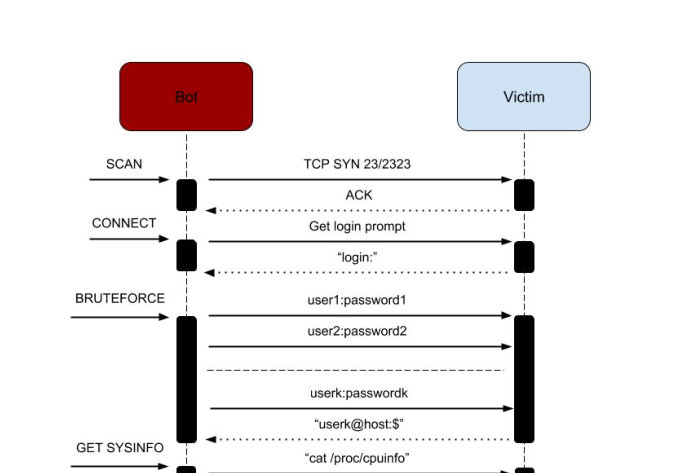 2018 has seen an increase in the variety of botnets living on the Internet of Things - such as Hide'N'Seek, which is notable for its use of peer-to-peer for command-and-control communication. Today, we publish the VB2018 paper by Bitdefender researchers Adrian Șendroiu and Vladimir Diaconescu, who studied the Hide'N'Seek IoT botnet. We also release the recording of their presentation.
2018 has seen an increase in the variety of botnets living on the Internet of Things - such as Hide'N'Seek, which is notable for its use of peer-to-peer for command-and-control communication. Today, we publish the VB2018 paper by Bitdefender researchers Adrian Șendroiu and Vladimir Diaconescu, who studied the Hide'N'Seek IoT botnet. We also release the recording of their presentation.
Posted by Martijn Grooten on Dec 4, 2018
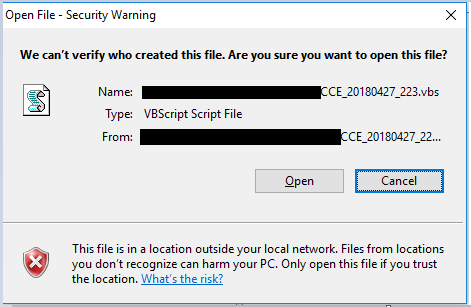 In a new paper, Avast researchers Jan Sirmer and Adolf Streda look at how a spam campaign sent via the Necurs botnet was delivering the Flawed Ammyy RAT. As well as publishing the paper, we have also released the video of the reseachers' VB2018 presentation on the same topic.
In a new paper, Avast researchers Jan Sirmer and Adolf Streda look at how a spam campaign sent via the Necurs botnet was delivering the Flawed Ammyy RAT. As well as publishing the paper, we have also released the video of the reseachers' VB2018 presentation on the same topic.