Posted by Martijn Grooten on May 15, 2018
 Through fake social media accounts, users were tricked into installing an Android application that was actually a mobile version of the FinFisher spyware.
Through fake social media accounts, users were tricked into installing an Android application that was actually a mobile version of the FinFisher spyware.
Posted by Martijn Grooten on May 9, 2018
 The Hide'n'Seek IoT botnet has received an update to make its infection persist on infected devices beyond a restart.
The Hide'n'Seek IoT botnet has received an update to make its infection persist on infected devices beyond a restart.
Posted by Martijn Grooten on May 8, 2018
 Registration for VB2018, the 28th International Virus Bulletin conference, is now open, with an early bird rate available until 1 July.
Registration for VB2018, the 28th International Virus Bulletin conference, is now open, with an early bird rate available until 1 July.
Posted by Martijn Grooten on May 1, 2018
 In April, VB's Martijn Grooten attended the RSA Expo in San Francisco. He shares his views on the expo and the industry.
In April, VB's Martijn Grooten attended the RSA Expo in San Francisco. He shares his views on the expo and the industry.
Posted by Martijn Grooten on Apr 30, 2018
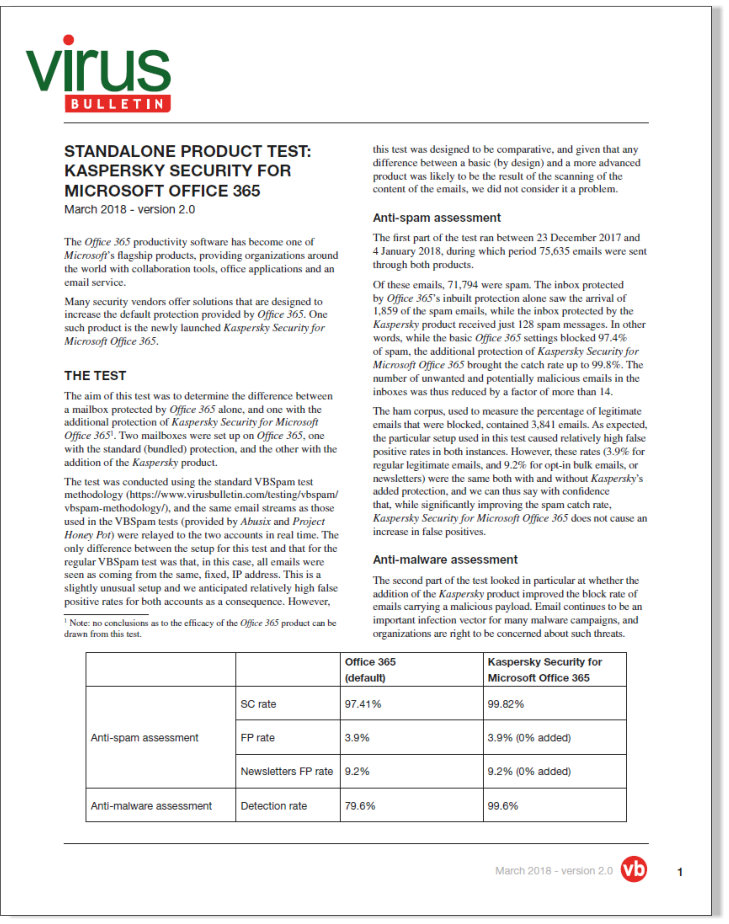 There are a number of security solutions on the market that are designed to increase the default protection provided by Office 365. One such product is the newly launched Kaspersky Security for Microsoft Office 365. Virus Bulletin was commissioned to measure the effectiveness of the Kaspersky product compared to the Office 365 baseline protection.
There are a number of security solutions on the market that are designed to increase the default protection provided by Office 365. One such product is the newly launched Kaspersky Security for Microsoft Office 365. Virus Bulletin was commissioned to measure the effectiveness of the Kaspersky product compared to the Office 365 baseline protection.
Posted by Martijn Grooten on Apr 27, 2018
 The GravityRAT malware, discovered by Cisco Talos researchers, gives some interesting insight into modern malware development.
The GravityRAT malware, discovered by Cisco Talos researchers, gives some interesting insight into modern malware development.
Posted by Martijn Grooten on Apr 25, 2018
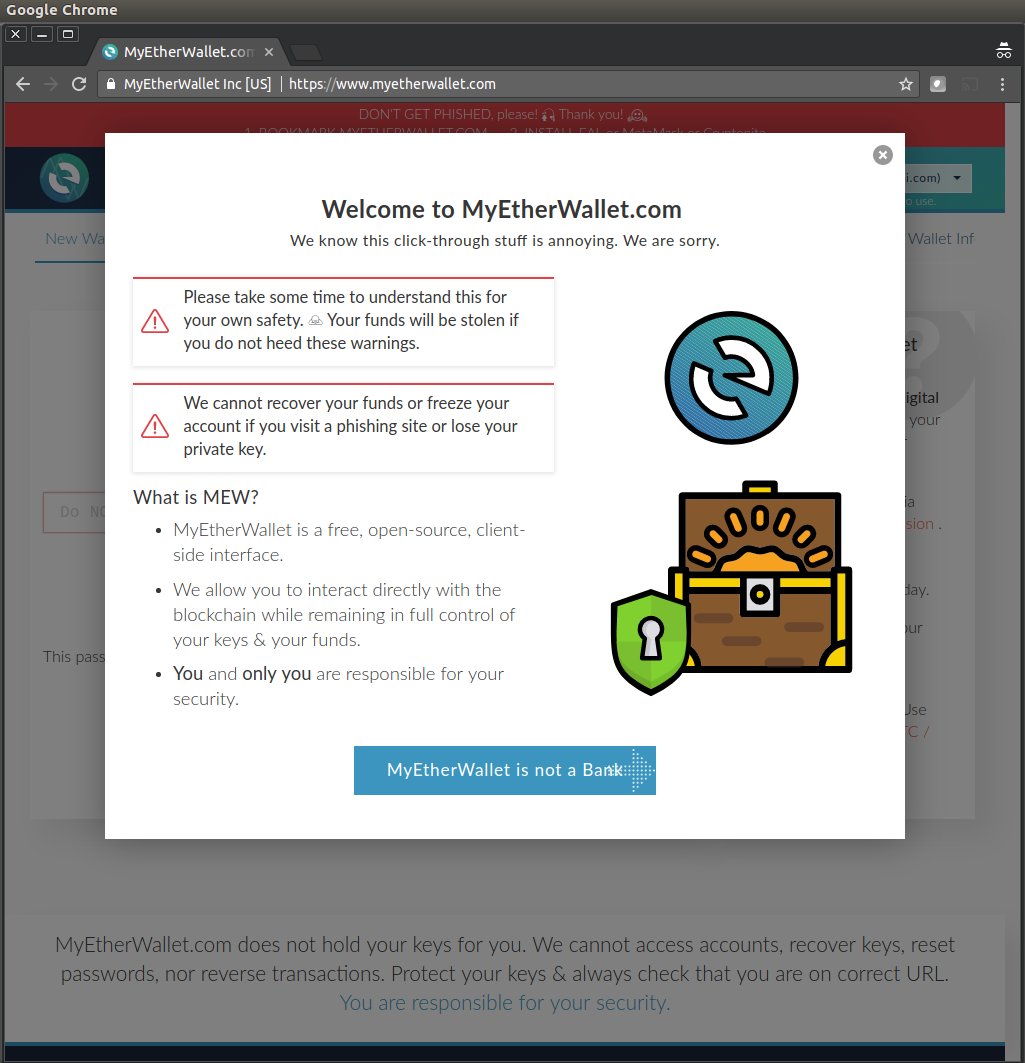 A BGP hijack was used to take over some of Amazon's DNS infrastructure, which was then used to serve a phishing site to users of the MyEtherWallet service.
A BGP hijack was used to take over some of Amazon's DNS infrastructure, which was then used to serve a phishing site to users of the MyEtherWallet service.
Posted by Martijn Grooten on Apr 24, 2018
 Various security companies are offering security-focused routers. This is a good trend and may help mitigate a lot of the issues that come with the IoT.
Various security companies are offering security-focused routers. This is a good trend and may help mitigate a lot of the issues that come with the IoT.
Posted by Virus Bulletin on Apr 23, 2018
 Most of the switch from IPv4 to IPv6 will happen seamlessly. But we cannot assume it won't introduce new security issues.
Most of the switch from IPv4 to IPv6 will happen seamlessly. But we cannot assume it won't introduce new security issues.
Posted by Martijn Grooten on Apr 19, 2018
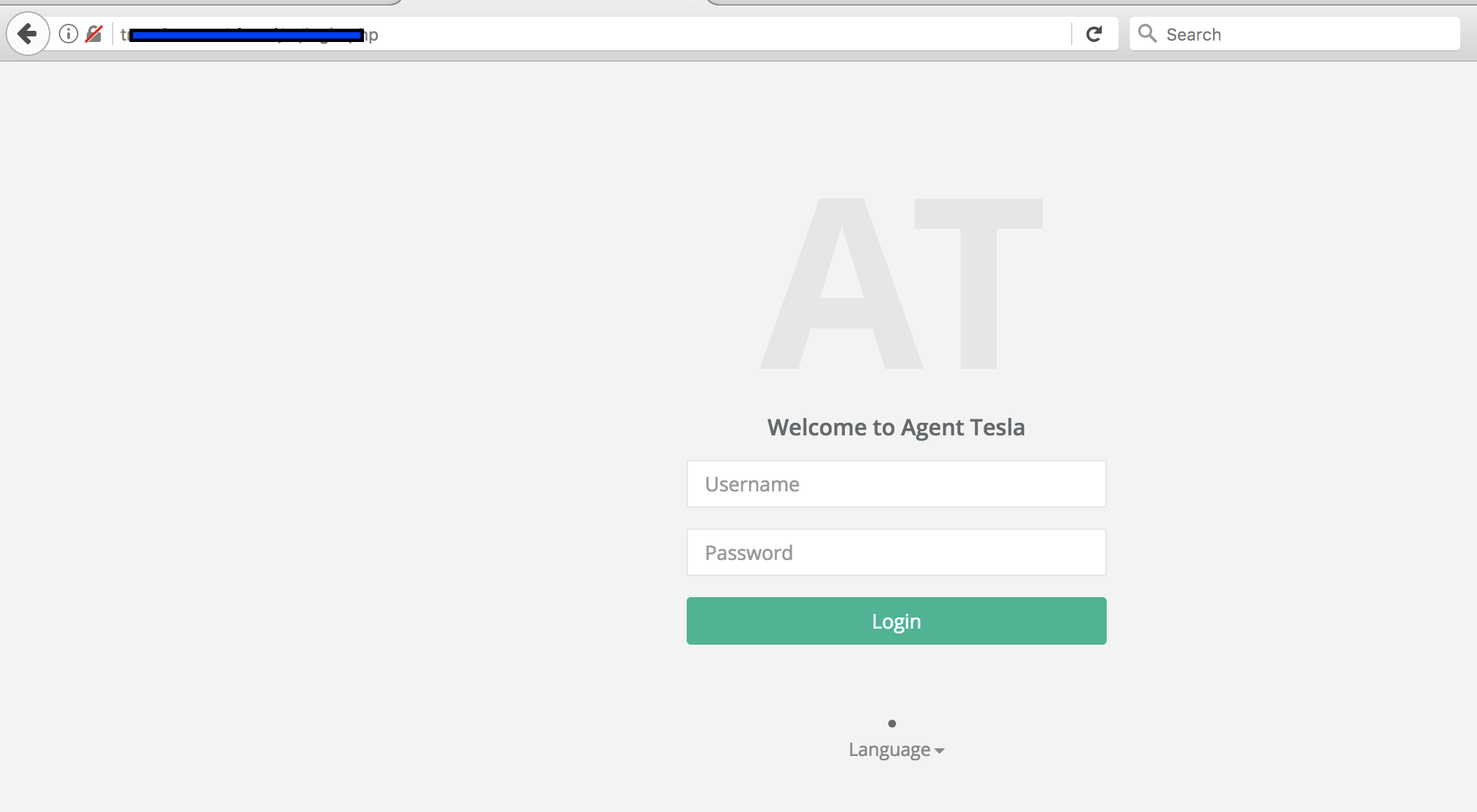 Since their return four years ago, Office macros have been one of the most common ways to spread malware. Today, we publish a research paper which looks in detail at a campaign in which VBA macros are used to execute PowerShell code, which in turn downloads the Tesla information-stealing trojan.
Since their return four years ago, Office macros have been one of the most common ways to spread malware. Today, we publish a research paper which looks in detail at a campaign in which VBA macros are used to execute PowerShell code, which in turn downloads the Tesla information-stealing trojan.