Posted by Virus Bulletin on Jan 14, 2020
 With the VB2020 Call for Papers now open, we explain how the selection procedure works, which may help you during your abstract submission.
With the VB2020 Call for Papers now open, we explain how the selection procedure works, which may help you during your abstract submission.
Posted by Virus Bulletin on Jan 13, 2020
 In 2019 we saw a rise in the number of targeted malware infections spread via ISPs and service providers. In a last-minute paper presented at VB2019 in London, Kaspersky researcher Denis Legezo discussed the details of a number of such cases. Today we release the recording of Denis' presentation.
In 2019 we saw a rise in the number of targeted malware infections spread via ISPs and service providers. In a last-minute paper presented at VB2019 in London, Kaspersky researcher Denis Legezo discussed the details of a number of such cases. Today we release the recording of Denis' presentation.
Posted by Virus Bulletin on Jan 10, 2020
 In a last-minute presentation at VB2019 in London, John Bambenek of the University of Illinois at Urbana-Champaign discussed details of campaigns that used advanced iOS and Android exploit chains against China’s Uighur minority. Today we release the recording of John's presentation.
In a last-minute presentation at VB2019 in London, John Bambenek of the University of Illinois at Urbana-Champaign discussed details of campaigns that used advanced iOS and Android exploit chains against China’s Uighur minority. Today we release the recording of John's presentation.
Posted by Helen Martin on Jan 8, 2020
 Today we released the Winter 2020 VBWeb report, detailing the performance of web security products against live web threats and looking at the current state of the web-based threat landscape.
Today we released the Winter 2020 VBWeb report, detailing the performance of web security products against live web threats and looking at the current state of the web-based threat landscape.
Posted by Virus Bulletin on Jan 6, 2020
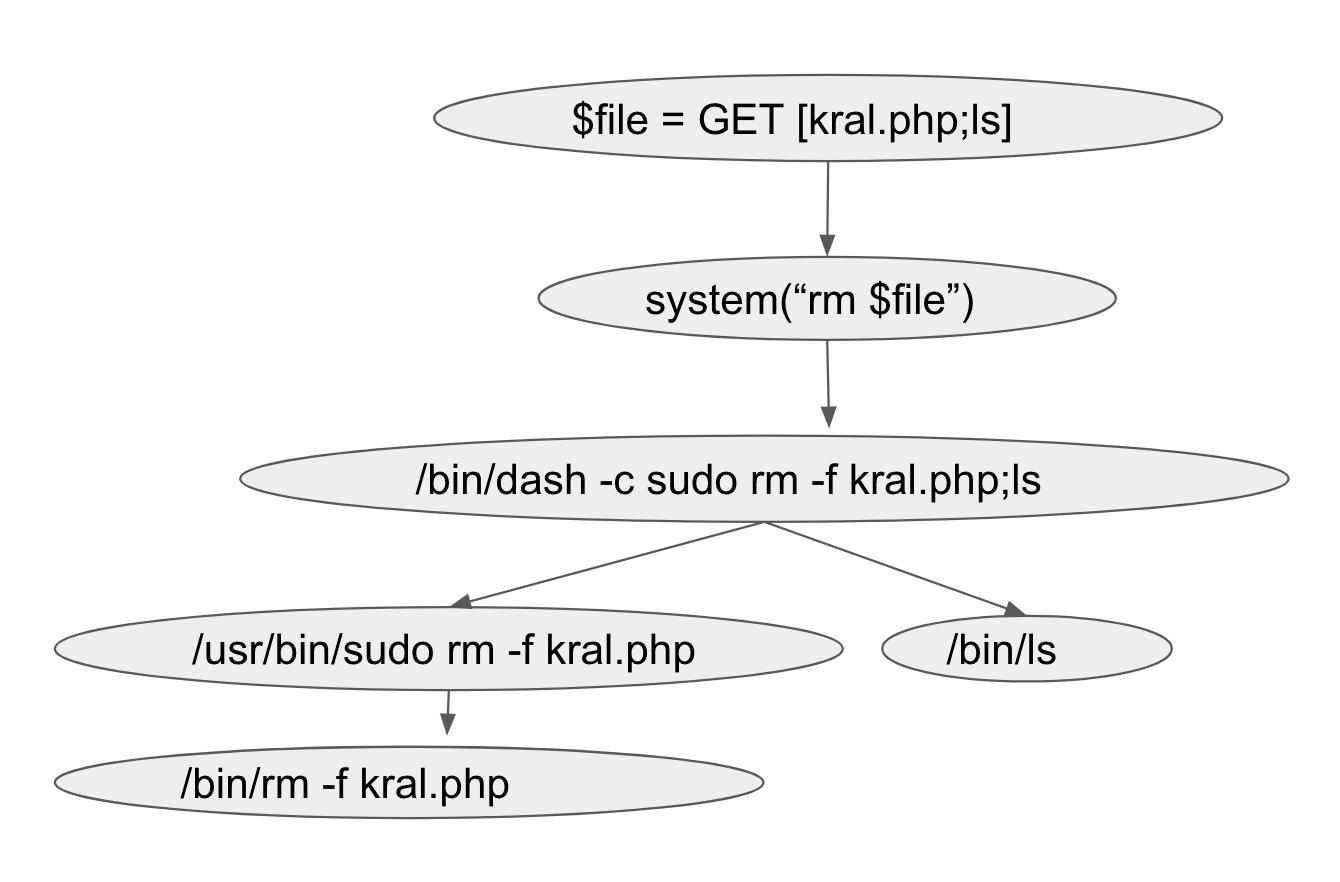 In a paper presented at VB2019 in London, Prismo Systems researchers Abhishek Singh and Ramesh Mani discussed code injection vulnerabilities and presented a tool that could detect this vulnerability class. Today we publish their paper and the recording of their presentation.
In a paper presented at VB2019 in London, Prismo Systems researchers Abhishek Singh and Ramesh Mani discussed code injection vulnerabilities and presented a tool that could detect this vulnerability class. Today we publish their paper and the recording of their presentation.
Posted by Helen Martin on Dec 31, 2019
 As VB Editor Martijn Grooten steps down from his role to move on to new challenges, the team wish him a fond farewell and the very best of luck in his future endeavours.
As VB Editor Martijn Grooten steps down from his role to move on to new challenges, the team wish him a fond farewell and the very best of luck in his future endeavours.
Posted by Martijn Grooten on Dec 27, 2019
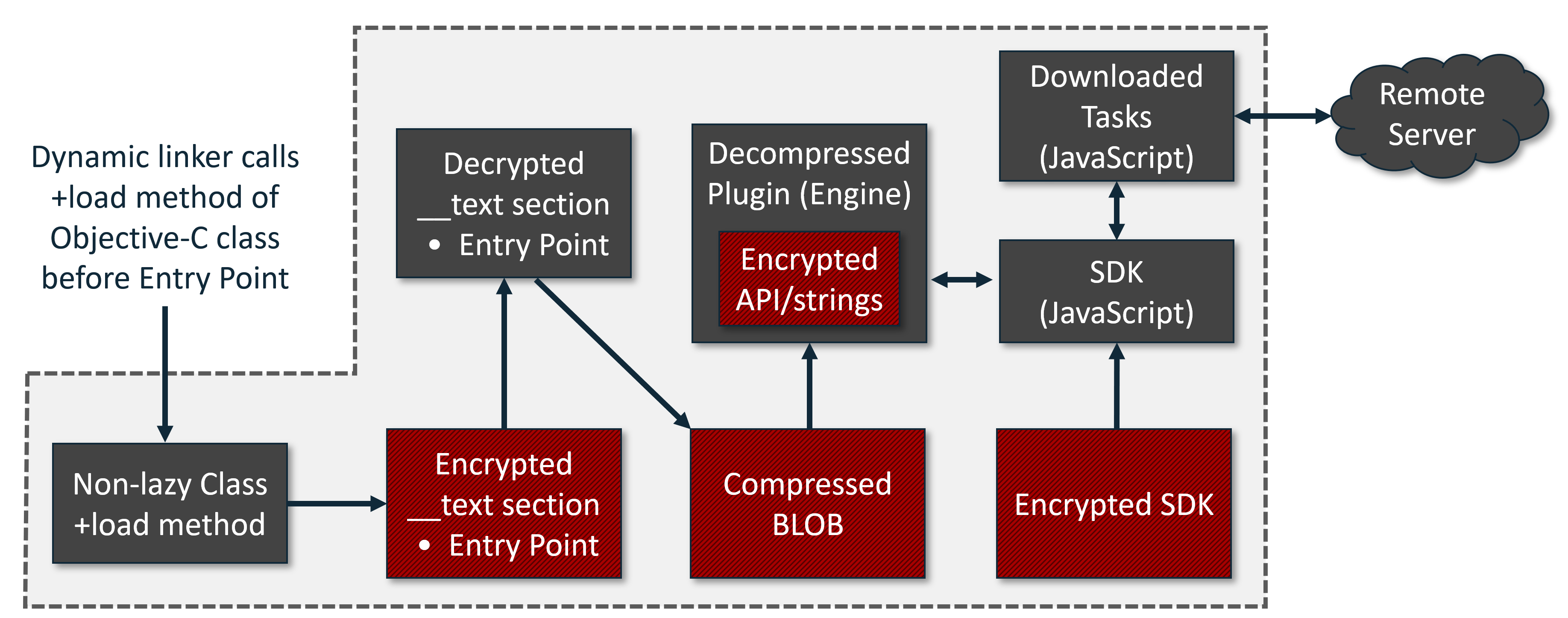 Today, we publish the VB2019 paper and video by Sophos researcher Sergei Shevchenko in which he analyses a popular yet unnamed piece of macOS ‘bundleware’.
Today, we publish the VB2019 paper and video by Sophos researcher Sergei Shevchenko in which he analyses a popular yet unnamed piece of macOS ‘bundleware’.
Posted by Martijn Grooten on Dec 23, 2019
 In the final of a five-part series of blog posts, departing VB Editor Martijn Grooten argues for more emphasis on the good news in security, especially that which is more subtle.
In the final of a five-part series of blog posts, departing VB Editor Martijn Grooten argues for more emphasis on the good news in security, especially that which is more subtle.
Posted by Virus Bulletin on Dec 20, 2019
 In the fourth of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why security researchers should refer to other people's work.
In the fourth of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why security researchers should refer to other people's work.
Posted by Martijn Grooten on Dec 19, 2019
 In the third of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why he believes security vendors should take their products' security more seriously.
In the third of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why he believes security vendors should take their products' security more seriously.