Posted by Martijn Grooten on Oct 30, 2018
 Cisco Talos researchers Paul Rascagnères and Warren Mercer were among the first to write about the Olympic Destroyer, the malware that targeted the 2018 PyeongChang Winter Olympic Games. Today, we publish the paper they presented at VB2018 about the malware; we also publish the video of their VB2018 presentation.
Cisco Talos researchers Paul Rascagnères and Warren Mercer were among the first to write about the Olympic Destroyer, the malware that targeted the 2018 PyeongChang Winter Olympic Games. Today, we publish the paper they presented at VB2018 about the malware; we also publish the video of their VB2018 presentation.
Posted by Martijn Grooten on Oct 26, 2018
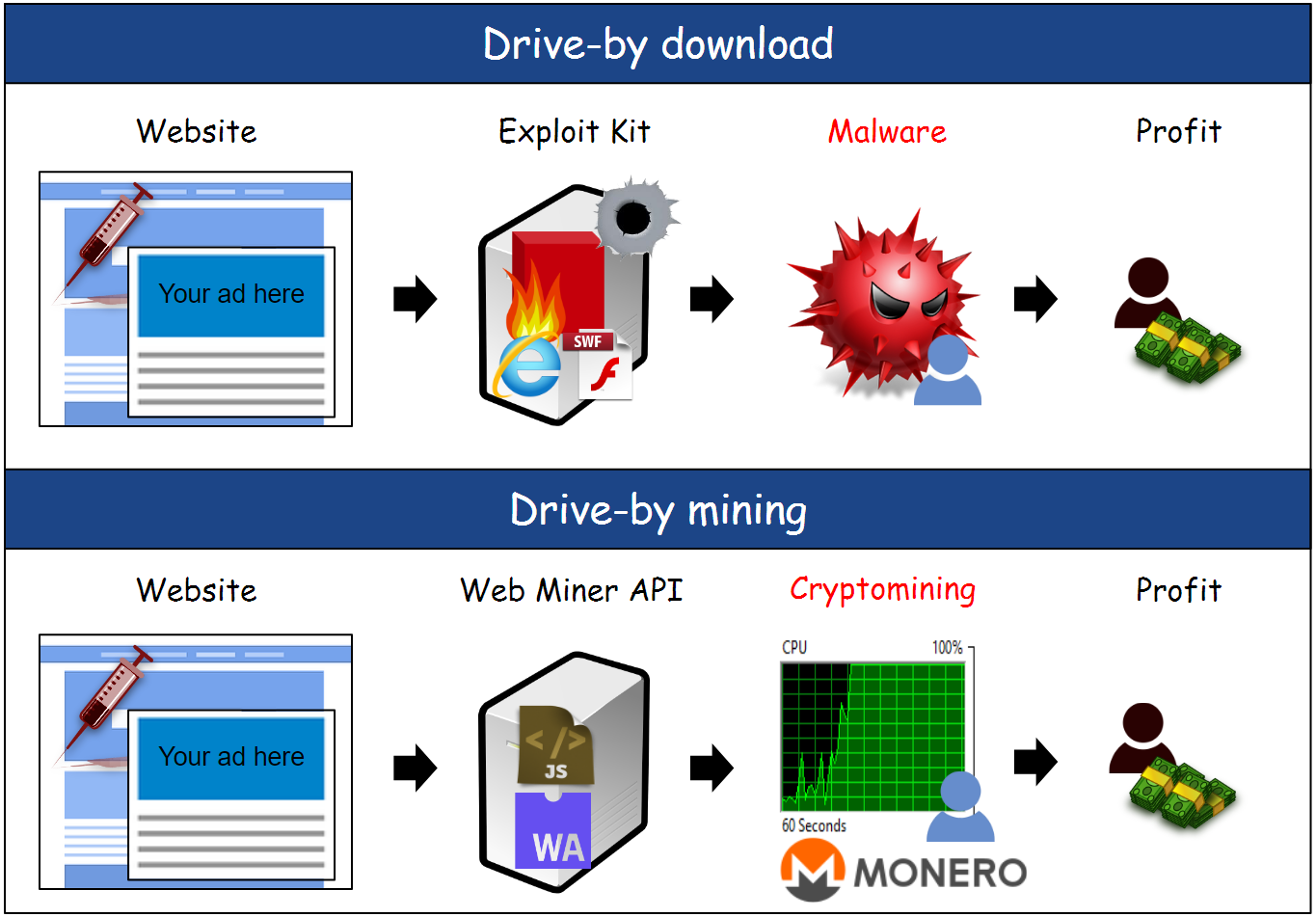 Today, we publish the VB2018 paper by Malwarebytes researcher Jérôme Segura, in which he details the shift from exploit kits to drive-by mining. We also publish the video of his VB2018 presentation.
Today, we publish the VB2018 paper by Malwarebytes researcher Jérôme Segura, in which he details the shift from exploit kits to drive-by mining. We also publish the video of his VB2018 presentation.
Posted by Martijn Grooten on Oct 22, 2018
 Today, we publish the video of the VB2018 presentation by CSIS researchers Benoît Ancel and Aleksejs Kuprins, who looked at a rather dubious seller of government spyware, described by someone else operating in the same space as a "criminal of the worst kind".
Today, we publish the video of the VB2018 presentation by CSIS researchers Benoît Ancel and Aleksejs Kuprins, who looked at a rather dubious seller of government spyware, described by someone else operating in the same space as a "criminal of the worst kind".
Posted by Virus Bulletin on Oct 17, 2018
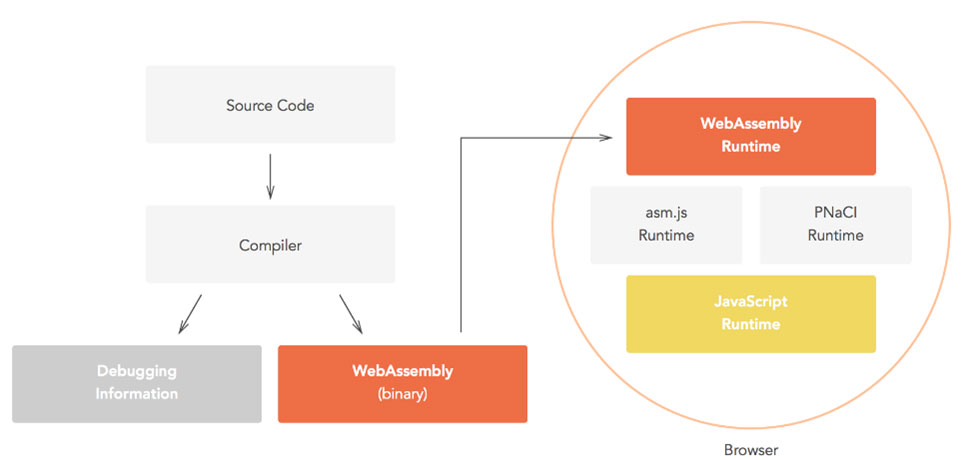 Today, we publish the VB2018 paper by Symantec researchers Aishwarya Lonkar and Siddhesh Chandrayan on the security risks that come with WebAssembly.
Today, we publish the VB2018 paper by Symantec researchers Aishwarya Lonkar and Siddhesh Chandrayan on the security risks that come with WebAssembly.
Posted by Martijn Grooten on Oct 5, 2018
 In 2019, the Virus Bulletin conference is set to return home, with VB2019 taking place in London, UK.
In 2019, the Virus Bulletin conference is set to return home, with VB2019 taking place in London, UK.
Posted by Virus Bulletin on Oct 2, 2018
 In a guest blog post, Kaspersky Lab's Anton Shingarev considers the case for increasing transparency in cybersecurity.
In a guest blog post, Kaspersky Lab's Anton Shingarev considers the case for increasing transparency in cybersecurity.
Posted by Martijn Grooten on Sep 28, 2018
 Workshops make their VB Conference debut during VB2018, giving delegates the opportunity to learn the basics of kernel-level malware analysis, Android reverse-engineering and artificial intelligence.
Workshops make their VB Conference debut during VB2018, giving delegates the opportunity to learn the basics of kernel-level malware analysis, Android reverse-engineering and artificial intelligence.
Posted by Martijn Grooten on Sep 27, 2018
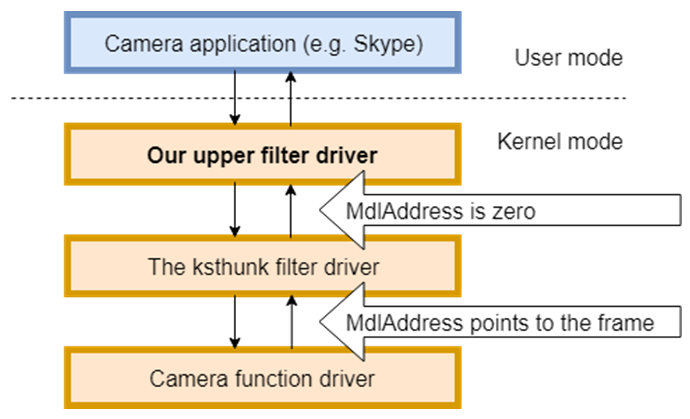 Today we publish a short article by Ronen Slavin and Michael Maltsev, researchers at Reason Software Company, who dive into the video capturing internals on Windows, and explain how this can be used by a malicious actor to steal images recorded by a computer's webcam.
Today we publish a short article by Ronen Slavin and Michael Maltsev, researchers at Reason Software Company, who dive into the video capturing internals on Windows, and explain how this can be used by a malicious actor to steal images recorded by a computer's webcam.
Posted by Martijn Grooten on Sep 27, 2018
 In a Small Talk at VB2018, Spamhaus's Simon Forster will present the organization's research into the botnet landscape and will discuss with the audience topics such as how the rise of anonymzation techniques and the hosting of botnets on well-regarded cloud providers have changed the landscape.
In a Small Talk at VB2018, Spamhaus's Simon Forster will present the organization's research into the botnet landscape and will discuss with the audience topics such as how the rise of anonymzation techniques and the hosting of botnets on well-regarded cloud providers have changed the landscape.
Posted by Virus Bulletin on Sep 26, 2018
 Virus Bulletin is proud to host the first Threat Intelligence Summit as an integral part of VB2018 next week. In a bid to help collect as much current data as possible, we'd like to ask anyone generating or consuming threat intelligence to fill in a very short survey.
Virus Bulletin is proud to host the first Threat Intelligence Summit as an integral part of VB2018 next week. In a bid to help collect as much current data as possible, we'd like to ask anyone generating or consuming threat intelligence to fill in a very short survey.