Posted by Martijn Grooten on Nov 1, 2019
 Those working in the field of infosec are often faced with ethical dilemmas that are impossible to avoid. Today, we publish a VB2019 paper by Kaspersky researcher Ivan Kwiatkowski looking at ethics in infosec as well as the recording of Ivan's presentation.
Those working in the field of infosec are often faced with ethical dilemmas that are impossible to avoid. Today, we publish a VB2019 paper by Kaspersky researcher Ivan Kwiatkowski looking at ethics in infosec as well as the recording of Ivan's presentation.
Posted by Martijn Grooten on Oct 31, 2019
 Malware used in domestic abuse situations is a growing threat, and the standard way for anti-virus products to handle such malware may not be good enough. But that doesn't mean there isn't an important role for anti-virus to play.
Malware used in domestic abuse situations is a growing threat, and the standard way for anti-virus products to handle such malware may not be good enough. But that doesn't mean there isn't an important role for anti-virus to play.
Posted by Martijn Grooten on Oct 28, 2019
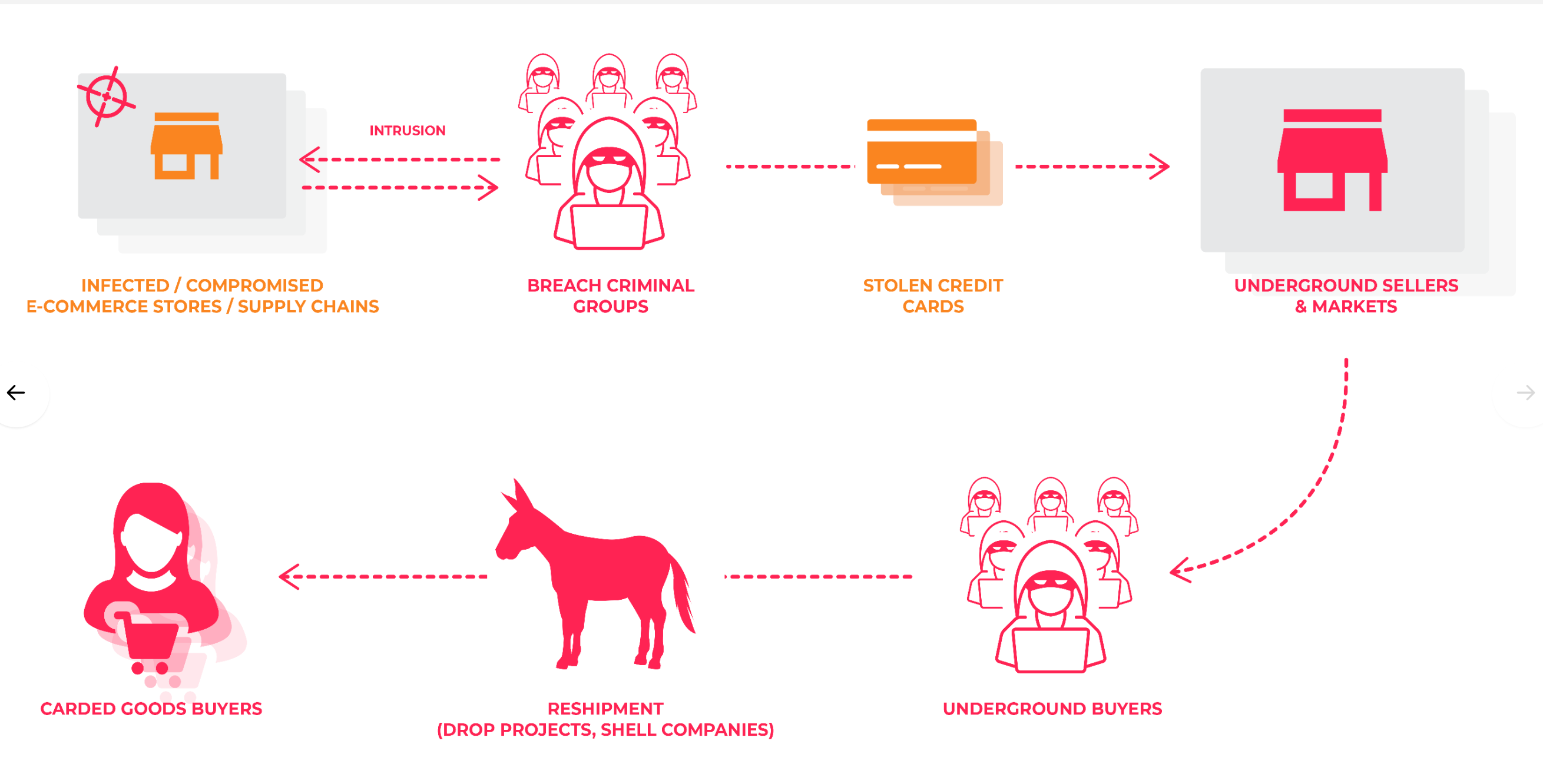 Today we publish the VB2019 paper by RiskIQ researcher Yonathan Klijnsma, who looked at the Magecart web-skimming attacks.
Today we publish the VB2019 paper by RiskIQ researcher Yonathan Klijnsma, who looked at the Magecart web-skimming attacks.
Posted by Martijn Grooten on Oct 25, 2019
Today, we publish the videos of the VB2019 partner presentations by Michael Maltsev (Reason Cybersecurity) on webcam interception and protection, and by Jean-Ian Boutin and Anton Cherepanov (ESET) on the Buhtrap group.
Read morePosted by Martijn Grooten on Oct 24, 2019
 The web continues to be a major infection vector for malware and credential-stealing threats. In the VBWeb tests, we measure products' ability to block such threats and certify products that perform a good job at doing so.
The web continues to be a major infection vector for malware and credential-stealing threats. In the VBWeb tests, we measure products' ability to block such threats and certify products that perform a good job at doing so.
Posted by Martijn Grooten on Oct 23, 2019
 Today we publish VB2019 papers by Luca Nagy (Sophos) on Emotet and Gabriela Nicolao and Luciano Martins (Deloitte) on Ryuk, as well as the corresponding videos of their presentations.
Today we publish VB2019 papers by Luca Nagy (Sophos) on Emotet and Gabriela Nicolao and Luciano Martins (Deloitte) on Ryuk, as well as the corresponding videos of their presentations.
Posted by Virus Bulletin on Oct 22, 2019
 The debate on responsible disclosure is about as old as IT security itself. In a guest post for Virus Bulletin Robert Neumann suggests we need to reconsider a one-size-fits-all solution and instead look for a well-respected independent organization to handle security issues.
The debate on responsible disclosure is about as old as IT security itself. In a guest post for Virus Bulletin Robert Neumann suggests we need to reconsider a one-size-fits-all solution and instead look for a well-respected independent organization to handle security issues.
Posted by Martijn Grooten on Oct 21, 2019
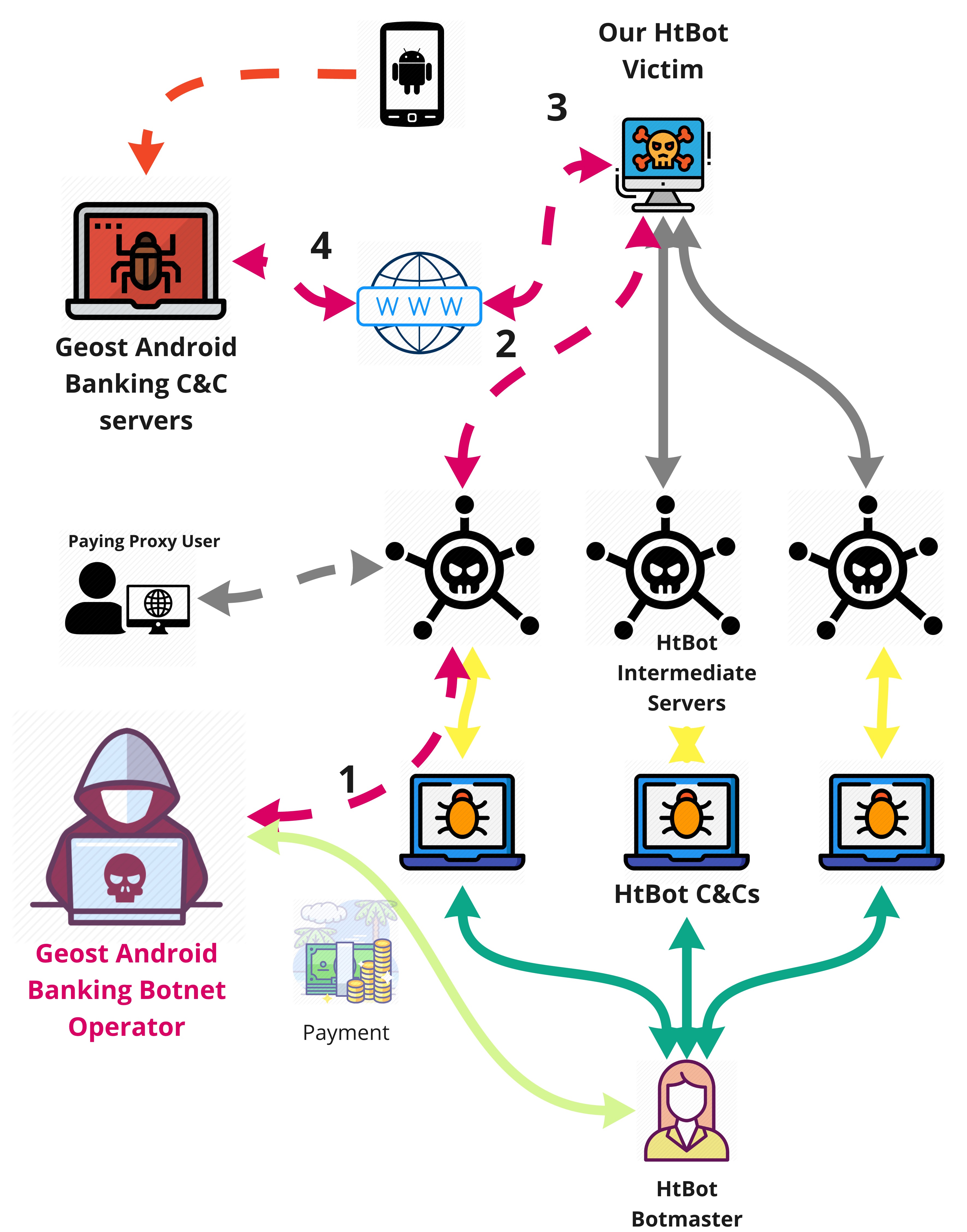 OpSec mistakes are what lead to many malware discoveries, and in the case of the Geost Android botnet the mistake was a really interesting one. Today we publish the VB2019 paper by Sebastian García, Maria Jose Erquiaga and Anna Shirokova on the Geost botnet, as well as the recording of Sebastian and Anna presenting their research in London.
OpSec mistakes are what lead to many malware discoveries, and in the case of the Geost Android botnet the mistake was a really interesting one. Today we publish the VB2019 paper by Sebastian García, Maria Jose Erquiaga and Anna Shirokova on the Geost botnet, as well as the recording of Sebastian and Anna presenting their research in London.
Posted by Virus Bulletin on Oct 14, 2019
 VB2019 Platinum partner Reason Cybersecurity presents a threat analysis report on the Save Yourself malware.
VB2019 Platinum partner Reason Cybersecurity presents a threat analysis report on the Save Yourself malware.
Posted by Virus Bulletin on Oct 4, 2019
 In a guest blog post VB2019 Platinum partner Reason Cybersecurity looks to the future of threat intelligence.
In a guest blog post VB2019 Platinum partner Reason Cybersecurity looks to the future of threat intelligence.