Posted by Helen Martin on Jan 5, 2017
 "Another year has come to its end and the malware battle still rages on." In January 2004, Jamz Yaneza reflected on the year just ended and pondered what the coming year would have in store for the AV industry.
"Another year has come to its end and the malware battle still rages on." In January 2004, Jamz Yaneza reflected on the year just ended and pondered what the coming year would have in store for the AV industry.
Posted by Martijn Grooten on Jan 4, 2017
At VB2016, ThreatConnect Director of Research Innovation Robert Simmons presented a paper on setting up an open source malware lab. Today, we share the accompanying paper and video.
Read morePosted by Martijn Grooten on Dec 24, 2016
As a Christmas present for the security community, we have uploaded most of the papers and videos from the VB2015 conference which took place in Prague almost 15 months ago. The Virus Bulletin crew wishes you all the best for 2017!
Read morePosted by Martijn Grooten on Dec 21, 2016
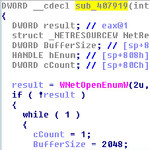 In a new paper published by Virus Bulletin, Acalvio researcher Abhishek Singh discusses some of the techniques used by malware to increase its impact by spreading further.
In a new paper published by Virus Bulletin, Acalvio researcher Abhishek Singh discusses some of the techniques used by malware to increase its impact by spreading further.
Posted by Martijn Grooten on Dec 20, 2016
 At VB2016, Kaspersky Lab researcher Kurt Baumgartner delivered a presentation on the StrongPity watering hole attacks that targeted users of encryption technologies, and which were recently featured in a report by Microsoft. Today, we share the video of Kurt's presentation.
At VB2016, Kaspersky Lab researcher Kurt Baumgartner delivered a presentation on the StrongPity watering hole attacks that targeted users of encryption technologies, and which were recently featured in a report by Microsoft. Today, we share the video of Kurt's presentation.
Posted by Martijn Grooten on Dec 20, 2016
 Three members of the Virus Bulletin team attended the Botconf 2016 conference in Lyon, France last month, enjoying talks on subjects that ranged from state-sponsored attacks to exploit kits, and from banking trojans to cyber insurance.
Three members of the Virus Bulletin team attended the Botconf 2016 conference in Lyon, France last month, enjoying talks on subjects that ranged from state-sponsored attacks to exploit kits, and from banking trojans to cyber insurance.
Posted by Helen Martin on Dec 15, 2016
 "Most of you reading this article have the technical skill but do you have the people skills?" In 2000, James Wolfe urged security experts to sell themselves and their services.
"Most of you reading this article have the technical skill but do you have the people skills?" In 2000, James Wolfe urged security experts to sell themselves and their services.
Posted by Martijn Grooten on Dec 12, 2016
Today, we publish the VB2016 paper and presentation (recording) by ESET researchers Jean-Ian Boutin and Anton Cherepanov, in which they look at sophisticated attacks against Russian financial institutions.
Read morePosted by Martijn Grooten on Dec 2, 2016
 At Botconf 2016 this week, GoSecure researchers Masarah Paquet-Clouston and Olivier Bilodeau presented their research on the Moose botnet - something Olivier Bilodeau previously spoke about at VB2015.
At Botconf 2016 this week, GoSecure researchers Masarah Paquet-Clouston and Olivier Bilodeau presented their research on the Moose botnet - something Olivier Bilodeau previously spoke about at VB2015.
Posted by Martijn Grooten on Dec 2, 2016
Today, we publish the VB2016 paper and presentation (recording) by Check Point Software researchers Alexander Chailytko and Stanislav Skuratovich, which focuses on the techniques used by malware to detect virtual environments, and provides detailed technical descriptions of what can be done to defeat them.
Read more