In a last-minute presentation at VB2019 in London, John Bambenek of the University of Illinois at Urbana-Champaign discussed details of campaigns that used advanced iOS and Android exploit chains against China’s Uighur minority. Today we release the recor…
One of the biggest security stories of 2019 was the use of advanced iOS and Android exploit chains against China’s Uighur minority, first uncovered by Google’s Project Zero with… https://www.virusbulletin.com/blog/2020/01/vb2019-presentation-deep-dive-iphone-exploit-chains/
At VB2019 in London, Check Point researchers Aseel Kayal and Lotem Finkelstein presented a paper detailing an Iranian operation they named 'Domestic Kitten' that used Android apps for targeted surveillance. Today we publish their paper and the video of th…
Domestic Kitten: an Iranian surveillance program
Read the paper (HTML)
Download the paper (PDF)
In September last year, researchers at Check Point uncovered… https://www.virusbulletin.com/blog/2019/11/vb2019-paper-d/
Virus Bulletin is excited to announce that, thanks to generous sponsorship from Google Android, we are able to offer 20 free tickets to students who want to attend VB2019.
Update 02 August 2019: Applications for free student tickets have now closed.
Virus Bulletin is excited to announce that, thanks to generous sponsorship from Google Android, we… https://www.virusbulletin.com/blog/2019/06/free-vb2019-tickets-students/
Workshops make their VB Conference debut during VB2018, giving delegates the opportunity to learn the basics of kernel-level malware analysis, Android reverse-engineering and artificial intelligence.
The Virus Bulletin Conference is first and foremost a place to learn: about new threats, about the tools used to detect and fight them, and to learn about (and get to know) the… https://www.virusbulletin.com/blog/2018/09/vb2018-preview-workshops/
It is likely that, by now, everyone in computer science has at least heard of the Spectre attack, and many excellent explanations of the attack already exist. But what is the likelihood of finding Spectre being exploited on Android smartphones?
The discovery of the Spectre and Meltdown attacks in January cast a long shadow over the year, with many of the issued security patches having their own problems and several new… https://www.virusbulletin.com/blog/2018/07/new-paper-does-malware-based-spectre-exist/
Within a few years, Android malware has grown from a relatively small threat to a huge problem involving more than three million new malware samples a year. Axelle Apvrille, one of the world's leading Android malware researchers, will deliver a workshop o…
Within a few years, Android malware has grown from a relatively small threat – the first VB conference talk on Android, in 2011, mentioned fewer than 100 malware families – to a… https://www.virusbulletin.com/blog/2018/04/vb2017-paper-android-reverse-engineering-tools-not-usual-suspects/
At VB2016 in Denver, Jorge Blasco presented a paper (co-written with Thomas M. Chen, Igor Muttik and Markus Roggenbach), in which he discussed the concept of app collusion - where two (or more) apps installed on the same device work together to collect an…
Playing out in the sidelines of the Cambridge Analytica scandal was the discovery that Facebook had been collecting metadata on the calls and SMS conversations of many of the… https://www.virusbulletin.com/blog/2018/03/vb2016-paper-wild-android-collusions/
From attacks on Ukraine's power grid to web shells, and from car hacking to ransomware: we announce the first nine 'last-minute' papers on the VB2017 programme.
At Virus Bulletin we try not to follow the daily security hype, focusing instead on the bigger trends. This means that the topics covered on the VB2017 conference programme – the… https://www.virusbulletin.com/blog/2017/09/vb2017-nine-last-minute-papers-announced/
Collaboration between a number of security companies has led to the takedown of the WireX Android DDoS botnet. Efforts like these, and the fact that the companies involved all decided to publish the very same blog post, show the best side of the security …
It is easy to be cynical about the security industry and its tendency to make ever bigger mountains out of molehills, but behind a thin layer of marketing, there are a great many… https://www.virusbulletin.com/blog/2017/08/wirex-ddos-botnet-takedown-shows-best-side-security-industry/
Full technical details of the first in-the-wild Android app 'collusion' attack, where multiple apps perform an attack in collaboration, will be shared with the public in
at VB2016 in Denver on 5 October.
Most research into and protection against malicious apps focuses on single apps. This makes it interesting for malware authors to use app 'collusion': the ability of two (or more)… https://www.virusbulletin.com/blog/2016/08/vb2016-preview-wild-android-collusions/
 Malware used in domestic abuse situations is a growing threat, and the standard way for anti-virus products to handle such malware may not be good enough. But that doesn't mean there isn't an important role for anti-virus to play.
Malware used in domestic abuse situations is a growing threat, and the standard way for anti-virus products to handle such malware may not be good enough. But that doesn't mean there isn't an important role for anti-virus to play.
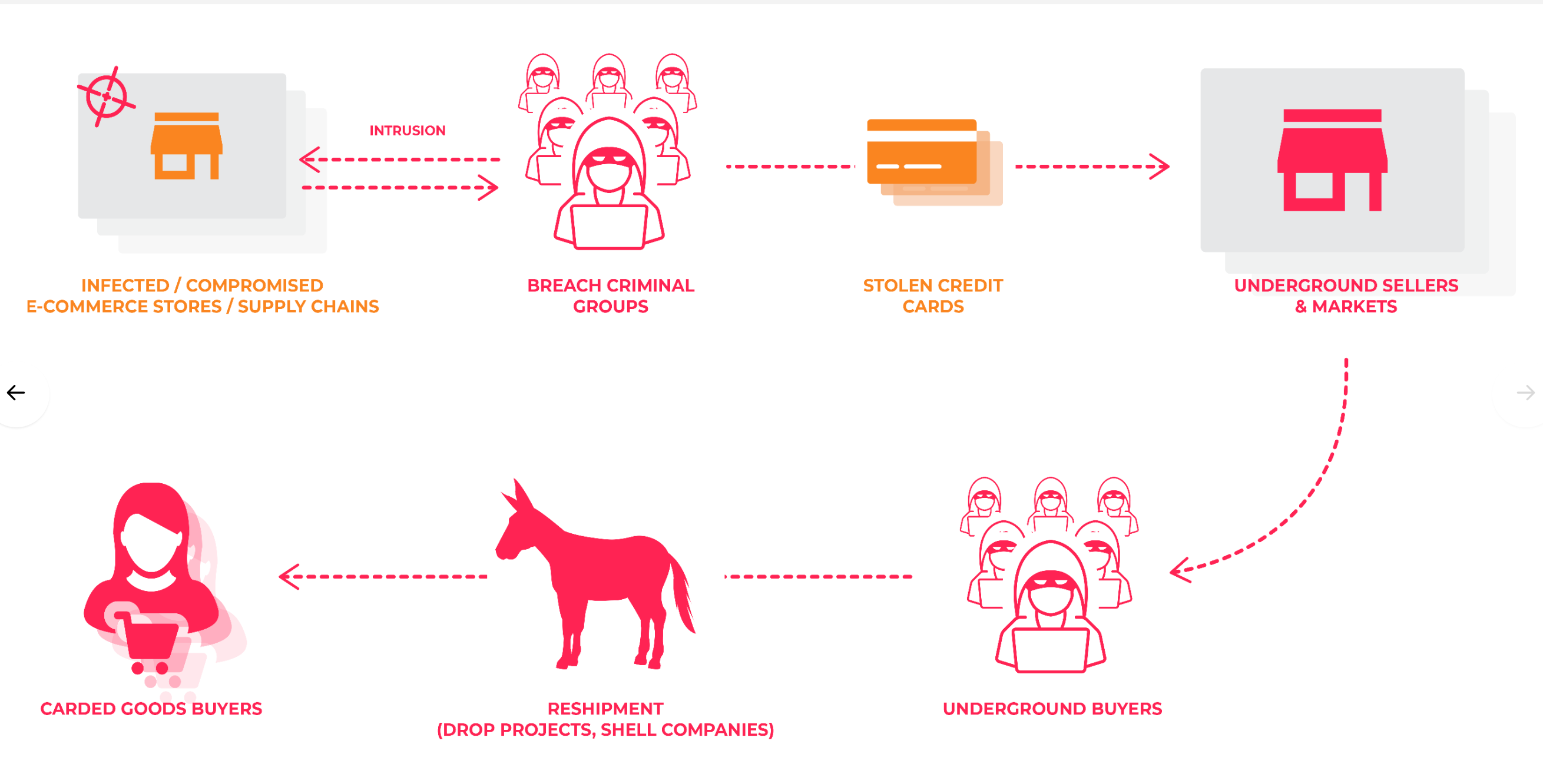 Today we publish the VB2019 paper by RiskIQ researcher Yonathan Klijnsma, who looked at the Magecart web-skimming attacks.
Today we publish the VB2019 paper by RiskIQ researcher Yonathan Klijnsma, who looked at the Magecart web-skimming attacks.
 The web continues to be a major infection vector for malware and credential-stealing threats. In the VBWeb tests, we measure products' ability to block such threats and certify products that perform a good job at doing so.
The web continues to be a major infection vector for malware and credential-stealing threats. In the VBWeb tests, we measure products' ability to block such threats and certify products that perform a good job at doing so.
 Today we publish VB2019 papers by Luca Nagy (Sophos) on Emotet and Gabriela Nicolao and Luciano Martins (Deloitte) on Ryuk, as well as the corresponding videos of their presentations.
Today we publish VB2019 papers by Luca Nagy (Sophos) on Emotet and Gabriela Nicolao and Luciano Martins (Deloitte) on Ryuk, as well as the corresponding videos of their presentations.
 The debate on responsible disclosure is about as old as IT security itself. In a guest post for Virus Bulletin Robert Neumann suggests we need to reconsider a one-size-fits-all solution and instead look for a well-respected independent organization to handle security issues.
The debate on responsible disclosure is about as old as IT security itself. In a guest post for Virus Bulletin Robert Neumann suggests we need to reconsider a one-size-fits-all solution and instead look for a well-respected independent organization to handle security issues.
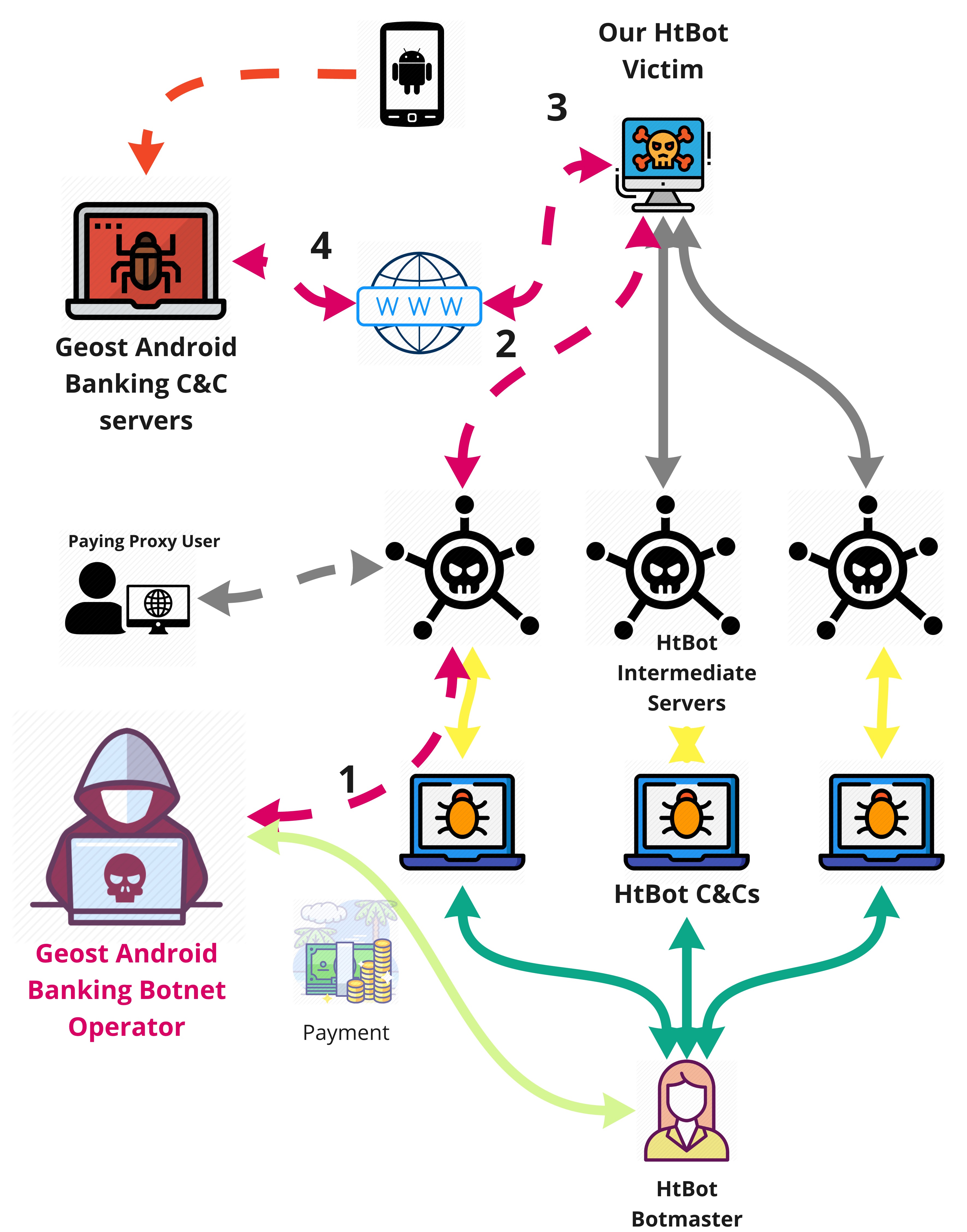 OpSec mistakes are what lead to many malware discoveries, and in the case of the Geost Android botnet the mistake was a really interesting one. Today we publish the VB2019 paper by Sebastian García, Maria Jose Erquiaga and Anna Shirokova on the Geost botnet, as well as the recording of Sebastian and Anna presenting their research in London.
OpSec mistakes are what lead to many malware discoveries, and in the case of the Geost Android botnet the mistake was a really interesting one. Today we publish the VB2019 paper by Sebastian García, Maria Jose Erquiaga and Anna Shirokova on the Geost botnet, as well as the recording of Sebastian and Anna presenting their research in London.
 VB2019 Platinum partner Reason Cybersecurity presents a threat analysis report on the Save Yourself malware.
VB2019 Platinum partner Reason Cybersecurity presents a threat analysis report on the Save Yourself malware.
 In a guest blog post VB2019 Platinum partner Reason Cybersecurity looks to the future of threat intelligence.
In a guest blog post VB2019 Platinum partner Reason Cybersecurity looks to the future of threat intelligence.
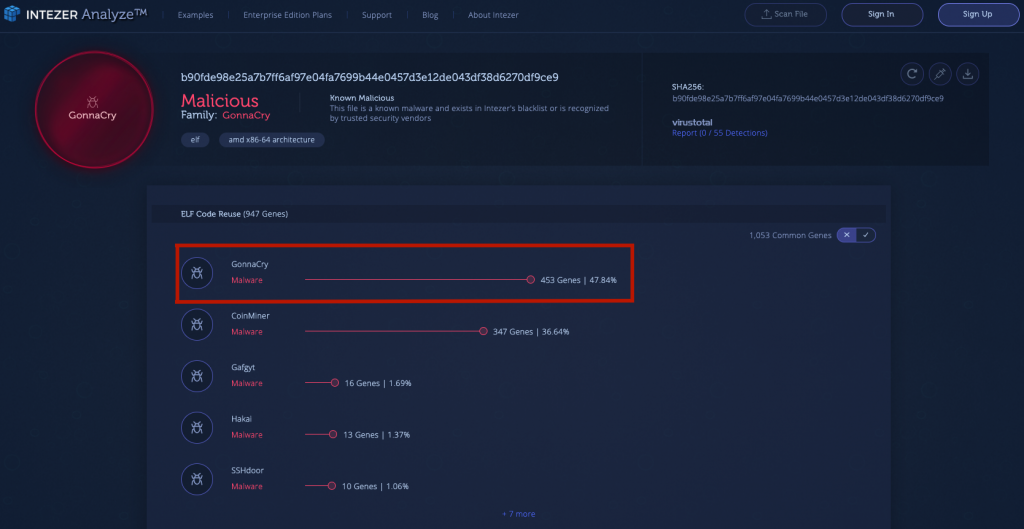 In a guest blog post VB2019 Silver partner Intezer outlines the importance of paying attention to Linux threats.
In a guest blog post VB2019 Silver partner Intezer outlines the importance of paying attention to Linux threats.