Posted by Martijn Grooten on Mar 15, 2016
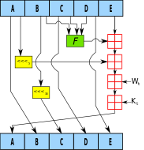 SHA-1 collisions may be found in the next few months, but that doesn't mean that fake SHA-1-based certificates will be created in the near future. Nevertheless, it is time for everyone, and those working in security in particular, to move away from outdated hash functions.
SHA-1 collisions may be found in the next few months, but that doesn't mean that fake SHA-1-based certificates will be created in the near future. Nevertheless, it is time for everyone, and those working in security in particular, to move away from outdated hash functions.
Posted by Martijn Grooten on Mar 11, 2016
 Are you interested in submitting an abstract for VB2016? We've answered some frequently asked questions about the Call for Papers, which closes next week.
Are you interested in submitting an abstract for VB2016? We've answered some frequently asked questions about the Call for Papers, which closes next week.
Posted by Helen Martin on Mar 10, 2016
 This Throwback Thursday we go back to 2004, when the entire crypto community was abuzz with the news that a group of Chinese researchers had demonstrated flaws in a whole set of hash functions - VB took a closer look to clarify the situation and draw lessons from the incident.
This Throwback Thursday we go back to 2004, when the entire crypto community was abuzz with the news that a group of Chinese researchers had demonstrated flaws in a whole set of hash functions - VB took a closer look to clarify the situation and draw lessons from the incident.
Posted by Martijn Grooten on Mar 2, 2016
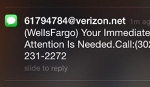 Though SMS may have been claimed dead many time, it is still very much alive, and quite popular among mobile phishers. At VB2015, Adaptive Mobile researcher Cathal Mc Daid presented a paper various mobile phishing campaigns targeting North American banks.
Though SMS may have been claimed dead many time, it is still very much alive, and quite popular among mobile phishers. At VB2015, Adaptive Mobile researcher Cathal Mc Daid presented a paper various mobile phishing campaigns targeting North American banks.
Posted by Helen Martin on Feb 25, 2016
 This Throwback Thursday VB heads back to 1996 when - long before the days of driveby downloads and exploit kits - VB published a report on the state of viruses on the Internet.
This Throwback Thursday VB heads back to 1996 when - long before the days of driveby downloads and exploit kits - VB published a report on the state of viruses on the Internet.
Posted by Martijn Grooten on Feb 24, 2016
 Next week, Virus Bulletin Editor Martijn Grooten will attend the RSA conference in San Francisco, where he will give a talk entitled "How Broken Is Our Crypto Really?" He will also speak at BSides San Francisco, where he will give a talk entitled "Elliptic Curve Cryptography for Those Who are Afraid of Mathematics".
Next week, Virus Bulletin Editor Martijn Grooten will attend the RSA conference in San Francisco, where he will give a talk entitled "How Broken Is Our Crypto Really?" He will also speak at BSides San Francisco, where he will give a talk entitled "Elliptic Curve Cryptography for Those Who are Afraid of Mathematics".
Posted by Martijn Grooten on Feb 19, 2016
 After a lot of preparation, Virus Bulletin is proud to have published the first "VBWeb" comparative web filter test report, in which products' ability to block web-based malware and drive-by downloads was tested. Fortinet's FortiGuard appliance was the first product to achieve a VBWeb certification.
After a lot of preparation, Virus Bulletin is proud to have published the first "VBWeb" comparative web filter test report, in which products' ability to block web-based malware and drive-by downloads was tested. Fortinet's FortiGuard appliance was the first product to achieve a VBWeb certification.
Posted by Martijn Grooten on Feb 18, 2016
 Sophos researchers Rowland Yu and William Lee look at whether recent security enhancements to Android, such as SEAndroid and containerization, will be enough to defeat future malware threats.
Sophos researchers Rowland Yu and William Lee look at whether recent security enhancements to Android, such as SEAndroid and containerization, will be enough to defeat future malware threats.
Posted by Martijn Grooten on Feb 17, 2016
 Virus Bulletin is excited to announce the first six sponsors for VB2016, the 26th international Virus Bulletin conference, which will take place in Denver, Colorado, USA 5-7 October 2016.
Virus Bulletin is excited to announce the first six sponsors for VB2016, the 26th international Virus Bulletin conference, which will take place in Denver, Colorado, USA 5-7 October 2016.
Posted by Martijn Grooten on Feb 11, 2016
 Cybercrime is big. But how big is it really? In a paper presented at VB2015 and together with the presentation video published on our website today, ESET researcher Stephen Cobb looks at previous studies that attempt the size of cybercrime and asks why we need such data and what can be done better.
Cybercrime is big. But how big is it really? In a paper presented at VB2015 and together with the presentation video published on our website today, ESET researcher Stephen Cobb looks at previous studies that attempt the size of cybercrime and asks why we need such data and what can be done better.