Posted by Martijn Grooten on Apr 24, 2017
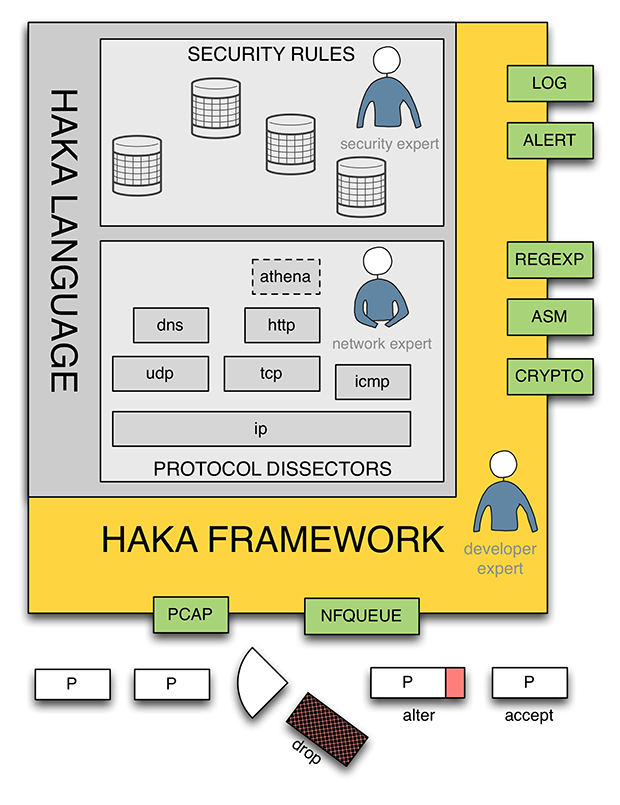 In their VB2016 paper, Stormshield researchers Benoît Ancel and Mehdi Talbi introduced Haka, an open-source language to monitor, debug and control malicious network traffic. Both their paper and the video recording of their presentation are now available to read/view on www.virusbulletin.com.
In their VB2016 paper, Stormshield researchers Benoît Ancel and Mehdi Talbi introduced Haka, an open-source language to monitor, debug and control malicious network traffic. Both their paper and the video recording of their presentation are now available to read/view on www.virusbulletin.com.
Posted by Martijn Grooten on Apr 13, 2017
We are proud to announce a very broad and very international programme for VB2017, which will take place in Madrid, 4-6 October 2017.
Read morePosted by Martijn Grooten on Apr 10, 2017
Virus Bulletin is excited to announce John-Graham Cumming and Brian Honan as the two keynote speakers for VB2017 in Madrid.
Read morePosted by Martijn Grooten on Mar 31, 2017
As VB's COO John Hawes moves on to new challenges, the team wish him a fond farewell and good luck in his future endeavours.
Read morePosted by Martijn Grooten on Mar 28, 2017
 Symantec researchers Himanshu Anand and Chastine Menrige explain how a single click can lead to a compromised machine, without malware ever being stored on disk.
Symantec researchers Himanshu Anand and Chastine Menrige explain how a single click can lead to a compromised machine, without malware ever being stored on disk.
Posted by Martijn Grooten on Mar 22, 2017
The Necurs botnet has started sending pump-and-dump spam. Almost all of these emails are blocked by spam filters, yet the stock price still increased.
Read morePosted by Martijn Grooten on Mar 10, 2017
Realistically speaking, if your software or system uses the SHA-1 hashing algorithm, it is unlikely that it will be exploited in the foreseeable future. But it is also extremely difficult to be certain that your system won't be the exception.
Read morePosted by Martijn Grooten on Mar 10, 2017
 The call for papers for VB2017, which takes place 4 to 6 October in Madrid, Spain, is currently open. We're always on the look out for new speakers and new content, so to help anyone who's unfamiliar with the VB conference, we've prepared a list of answers to some frequently asked questions about the event, and about how to submit a paper.
The call for papers for VB2017, which takes place 4 to 6 October in Madrid, Spain, is currently open. We're always on the look out for new speakers and new content, so to help anyone who's unfamiliar with the VB conference, we've prepared a list of answers to some frequently asked questions about the event, and about how to submit a paper.
Posted by Helen Martin on Mar 9, 2017
 This week marked the 25th anniversary of the trigger date of the infamous Michelangelo virus. In January 1992, VB published an analysis of the boot sector virus that captured the imagination of the press and kicked up a media storm.
This week marked the 25th anniversary of the trigger date of the infamous Michelangelo virus. In January 1992, VB published an analysis of the boot sector virus that captured the imagination of the press and kicked up a media storm.
Posted by Martijn Grooten on Mar 8, 2017
 Is it your job to defend your company’s network? Are you defending a government’s systems? Do you help secure the devices used by activists operating in less open societies? Do you work with abuse victims targeted by spyware? Share your experiences with the security community at VB2017.
Is it your job to defend your company’s network? Are you defending a government’s systems? Do you help secure the devices used by activists operating in less open societies? Do you work with abuse victims targeted by spyware? Share your experiences with the security community at VB2017.