Posted by Martijn Grooten on Feb 11, 2016
 Cybercrime is big. But how big is it really? In a paper presented at VB2015 and together with the presentation video published on our website today, ESET researcher Stephen Cobb looks at previous studies that attempt the size of cybercrime and asks why we need such data and what can be done better.
Cybercrime is big. But how big is it really? In a paper presented at VB2015 and together with the presentation video published on our website today, ESET researcher Stephen Cobb looks at previous studies that attempt the size of cybercrime and asks why we need such data and what can be done better.
Posted by Helen Martin on Feb 11, 2016
 This Throwback Thursday, VB heads back to 1994 when UK Fraud Squad detectives started making inroads into the most puzzling 'Whodunnit' since the Great Train Robbery. Had an outbreak of computer crime swept Britain? No, it was all part of a police training program.
This Throwback Thursday, VB heads back to 1994 when UK Fraud Squad detectives started making inroads into the most puzzling 'Whodunnit' since the Great Train Robbery. Had an outbreak of computer crime swept Britain? No, it was all part of a police training program.
Posted by Martijn Grooten on Feb 10, 2016
 Almost 20 years after Virus Bulletin revealed its first site on the "world wide web", we've redesigned our whole website. And we have a new domain as well.
Almost 20 years after Virus Bulletin revealed its first site on the "world wide web", we've redesigned our whole website. And we have a new domain as well.
Posted by Virus Bulletin on Feb 9, 2016
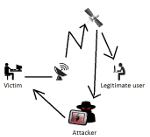 In a presentation at VB2015 in Prague, Kaspersky Lab researcher Kurt Baumgartner talked about Turla's extraplanetary activities: the malware used (and abused) satellite Internet connections for command and control communication.
In a presentation at VB2015 in Prague, Kaspersky Lab researcher Kurt Baumgartner talked about Turla's extraplanetary activities: the malware used (and abused) satellite Internet connections for command and control communication.
Posted by Virus Bulletin on Feb 1, 2016
 When interviewed by the Risky Business podcast last week, VB Editor Martijn Grooten talked about the security of security products and said that many vendors are embracing the work done by Tavis Ormandy and others - as they should.
When interviewed by the Risky Business podcast last week, VB Editor Martijn Grooten talked about the security of security products and said that many vendors are embracing the work done by Tavis Ormandy and others - as they should.
Posted by Virus Bulletin on Jan 29, 2016
 More VB2014 Conference papers and videos published - 11 papers and 9 videos added to our website.
More VB2014 Conference papers and videos published - 11 papers and 9 videos added to our website.
Posted by Virus Bulletin on Jan 28, 2016
 This Throwback Thursday, VB heads back to 1993, when an ordinary memory-resident master boot sector virus spiced things up with a bit of pop trivia.
This Throwback Thursday, VB heads back to 1993, when an ordinary memory-resident master boot sector virus spiced things up with a bit of pop trivia.
Posted by Virus Bulletin on Jan 27, 2016
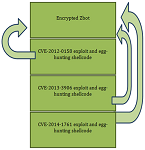 Simon Edwards discusses how to test the potentially untestable.
Simon Edwards discusses how to test the potentially untestable.
Posted by Virus Bulletin on Jan 21, 2016
 Juan Andrés Guerrero-Saade discusses the perils and ethical conundrums that arise as the industry enters a new playing field.
Juan Andrés Guerrero-Saade discusses the perils and ethical conundrums that arise as the industry enters a new playing field.
Posted by Virus Bulletin on Jan 19, 2016
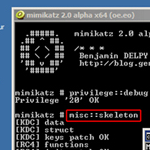 Microsoft, Dell SecureWorks researchers analyse malware targeting Active Directory servers.
Microsoft, Dell SecureWorks researchers analyse malware targeting Active Directory servers.