Posted by Martijn Grooten on Aug 22, 2017
 At VB2017, Cloudflare's Head of Cryptography Nick Sullivan will give a Small Talk on the intercepting of HTTPS connections by proxies and anti-virus software.
At VB2017, Cloudflare's Head of Cryptography Nick Sullivan will give a Small Talk on the intercepting of HTTPS connections by proxies and anti-virus software.
Posted by Virus Bulletin on Aug 10, 2017
 In the second part of this two-part blog series, we look at five more memorable Virus Bulletin conference presentations.
In the second part of this two-part blog series, we look at five more memorable Virus Bulletin conference presentations.
Posted by Martijn Grooten on Aug 9, 2017
With the VB2017 Call for Papers out, here are five tips to increase your chances of getting your submission accepted.
Read morePosted by Martijn Grooten on Aug 8, 2017
Following the arrest of WannaCry hero Marcus Hutchings, suggestions have been made that he was behind the WannaCry malware itself, and that he inserted the kill switch to make himself a hero. This seems highly unlikely.
Read morePosted by Martijn Grooten on Aug 3, 2017
 In a two-part blog post series, we look back at ten memorable VB conference presentations from the past ten years.
In a two-part blog post series, we look back at ten memorable VB conference presentations from the past ten years.
Posted by Martijn Grooten on Aug 3, 2017
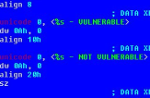 The authors of the Trickbot banking trojan seem to have taken note of the use of SMB by WannaCry and (Not)Petya and have added an (experimental) module that uses SMB for lateral movement.
The authors of the Trickbot banking trojan seem to have taken note of the use of SMB by WannaCry and (Not)Petya and have added an (experimental) module that uses SMB for lateral movement.
Posted by Martijn Grooten on Aug 1, 2017
 To give those attending VB2017 Madrid a chance to experience a little bit of the host city, the VB2017 drinks reception will be held at the unique and fascinating Geographic Club.
To give those attending VB2017 Madrid a chance to experience a little bit of the host city, the VB2017 drinks reception will be held at the unique and fascinating Geographic Club.
Posted by Martijn Grooten on Aug 1, 2017
To comply with Chinese laws, Apple has removed all iOS VPN apps from its Chinese app store. This means that the company uses iOS's strongest security asset, its tightly controlled App Store, against its own users.
Read morePosted by Martijn Grooten on Jul 28, 2017
 Today we announce the first two Small Talks for the VB2017 programme: ENISA will provide its perspective on the WannaCry outbreak and the lessons learned from it, while David Harley will talk about the past and present of security product testing.
Today we announce the first two Small Talks for the VB2017 programme: ENISA will provide its perspective on the WannaCry outbreak and the lessons learned from it, while David Harley will talk about the past and present of security product testing.
Posted by Martijn Grooten on Jul 27, 2017
 This week the NoMoreRansom project celebrated its first birthday. It has already helped many victims of ransomware with advice and tools and is an excellent example of collaboration between private and public partners in IT security.
This week the NoMoreRansom project celebrated its first birthday. It has already helped many victims of ransomware with advice and tools and is an excellent example of collaboration between private and public partners in IT security.