The call for papers for VB2018 closes on 18 March, and while we've already received many great submissions, we still want more! Here are five reasons why you should submit a paper this weekend.
The call for papers for VB2018 will close this Sunday, 18 March (in fact, to ensure we cover the entirety of the deadline day across all time zones, we'll close submissions first… https://www.virusbulletin.com/blog/2018/03/five-reasons-submit-vb2018-paper-weekend/
Partnering with the VB conference links your company to a successful and well-established event, demonstrates your commitment to moving the industry forward, allows you to meet potential clients, be visible to industry peers and build lasting connections.…
Preparations are under way for VB2018, or to give it its full name, the 28th Virus Bulletin International Conference – it truly is a global event, attracting speakers and… https://www.virusbulletin.com/blog/2018/03/partner-vb2018-extra-visibility-among-industry-peers/
At VB2017 in Madrid, security researcher Himanshu Anand presented a paper on malware that targets routers, looking both at the topic in general and at some individual case studies. Today we publish both the paper (co-written with Chastine Menrige) and the…
In recent years, we have seem a significant increase in malware targeting routers. Given that, unlike most endpoint devices, routers are often connected directly to the internet,… https://www.virusbulletin.com/blog/2018/03/vb2017-paper-router-all-evil/
Though many of the IT security issues we face are global, there is a noticeable difference in the threats faced in various countries and regions, as well as in the ways they are dealt with. At VB2017, we heard from Tyrus Kamau about the state of cybersecu…
IT security, or the lack thereof, affects Internet users around the world, and though many of the issues we face are global, there is a noticeable difference in the threats faced… https://www.virusbulletin.com/blog/2018/03/vb2017-video-state-cybersecurity-africa-kenya/
We especially encourage those less experienced in speaking in public to submit to the call for papers for VB2018, where we aim to provide a friendly and welcoming environment in which people can both present their own research and learn from what others h…
Last week, we opened the Call for Papers for VB2018, the 28th Virus Bulletin International Conference, which will take place in Montreal, 3-5 October this year. Over the years,… https://www.virusbulletin.com/blog/2018/01/first-time-speaker-we-hope-you-submit-vb2018-cfp/
At VB2017 in Madrid, security researcher Randy Abrams presented an overview of the VirusTotal service and then went on to bust several of the persistent myths that surround it. Today we publish both Randy's paper and the recording of his presentation.
In a surprise announcement, Google's parent company Alphabet has introduced Chronicle, a threat intelligence offering in which Google-owned VirusTotal will play an important role.… https://www.virusbulletin.com/blog/2018/01/vb2017-paper-virustotal-tips-tricks-and-myths/
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2018 is now open and we want to hear from you!
The call for papers for VB2018, the 28th Virus Bulletin International Conference, which will take place in Montreal, Canada, 3-5 October 2018, is now open!
We welcome… https://www.virusbulletin.com/blog/2018/01/vb2018-call-papers/
Martijn Grooten reports on the 20th AVAR conference, which took place earlier in December in Beijing, China.
The first week of December was packed with security conferences, and VB2017 speakers were busy presenting their research at no fewer than four different events: FIRST in Prague,… https://www.virusbulletin.com/blog/2017/12/conference-review-avar-2017/
Virus Bulletin researchers report back from a very interesting fifth edition of Botconf, the botnet fighting conference.
Since its first edition in 2013, the Virus Bulletin team have been big fans of Botconf, the botnet fighting conference held every year in France. This year, Virus Bulletin sent… https://www.virusbulletin.com/blog/2017/12/conference-review-botconf-2017/
(In)security is a global issue that affects countries around the world, but in recent years none has been so badly hit as Ukraine. Today, we publish the videos of two VB2017 talks about attacks that hit Ukraine particularly badly: a talk by Alexander Adam…
(In)security is a global problem that affects every country in the world, but in recent years, none has been as badly hit as Ukraine.
The most well known malware that… https://www.virusbulletin.com/blog/2017/12/vb2017-videos-attacks-against-ukraine/
Cerber is one of the major names in the world of ransomware, and last year, Check Point released a decryption service for the malware. Today, we publish a VB2017 paper by Check Point's Stanislav Skuratovich describing how the Cerber decryption tool worked…
Earlier this week, we published the video of a VB2017 presentation on the Spora ransomware. Spora is hardly alone in this prominent threat type though, and one of the other major… https://www.virusbulletin.com/blog/2017/12/vb2017-paper-nine-circles-cerber/
During recent research, Cisco Talos researchers observed the ways in which APT actors are evolving and how a reconnaissance phase is included in the infection vector in order to protect valuable zero-day exploits or malware frameworks. At VB2017 in Madrid…
Targeted attack campaigns involve multiple stages, the first of which consists of collecting information about the target: the reconnaissance phase. It's an essential part of any… https://www.virusbulletin.com/blog/2017/12/vb2017-paper-modern-reconnaissance-phase-apt-protection-layer/
At VB2017 in Madrid, CERT Poland researchers Maciej Kotowicz and Jarosław Jedynak presented a paper detailing their low-level analysis of five spam botnets. Today we publish their full paper.
Spam continues to be an important infection vector for many malware campaigns, but while a lot of attention is paid to the payloads delivered by these campaigns – Andrew Brandt's… https://www.virusbulletin.com/blog/2017/12/vb2017-paper-peering-spam-botnets/
 "Another year has come to its end and the malware battle still rages on." In January 2004, Jamz Yaneza reflected on the year just ended and pondered what the coming year would have in store for the AV industry.
"Another year has come to its end and the malware battle still rages on." In January 2004, Jamz Yaneza reflected on the year just ended and pondered what the coming year would have in store for the AV industry.
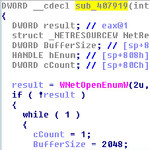 In a new paper published by Virus Bulletin, Acalvio researcher Abhishek Singh discusses some of the techniques used by malware to increase its impact by spreading further.
In a new paper published by Virus Bulletin, Acalvio researcher Abhishek Singh discusses some of the techniques used by malware to increase its impact by spreading further.
 At VB2016, Kaspersky Lab researcher Kurt Baumgartner delivered a presentation on the StrongPity watering hole attacks that targeted users of encryption technologies, and which were recently featured in a report by Microsoft. Today, we share the video of Kurt's presentation.
At VB2016, Kaspersky Lab researcher Kurt Baumgartner delivered a presentation on the StrongPity watering hole attacks that targeted users of encryption technologies, and which were recently featured in a report by Microsoft. Today, we share the video of Kurt's presentation.
 Three members of the Virus Bulletin team attended the Botconf 2016 conference in Lyon, France last month, enjoying talks on subjects that ranged from state-sponsored attacks to exploit kits, and from banking trojans to cyber insurance.
Three members of the Virus Bulletin team attended the Botconf 2016 conference in Lyon, France last month, enjoying talks on subjects that ranged from state-sponsored attacks to exploit kits, and from banking trojans to cyber insurance.
 "Most of you reading this article have the technical skill but do you have the people skills?" In 2000, James Wolfe urged security experts to sell themselves and their services.
"Most of you reading this article have the technical skill but do you have the people skills?" In 2000, James Wolfe urged security experts to sell themselves and their services.
 At Botconf 2016 this week, GoSecure researchers Masarah Paquet-Clouston and Olivier Bilodeau presented their research on the Moose botnet - something Olivier Bilodeau previously spoke about at VB2015.
At Botconf 2016 this week, GoSecure researchers Masarah Paquet-Clouston and Olivier Bilodeau presented their research on the Moose botnet - something Olivier Bilodeau previously spoke about at VB2015.