Posted by Martijn Grooten on Jun 25, 2018
 If you want to come to VB2018 in Montreal this year (and why wouldn't you?) and want to save a bit on the ticket price (and why wouldn't you?), remember that early bird discounts will be available until 30 June.
If you want to come to VB2018 in Montreal this year (and why wouldn't you?) and want to save a bit on the ticket price (and why wouldn't you?), remember that early bird discounts will be available until 30 June.
Posted by Martijn Grooten on Jun 21, 2018
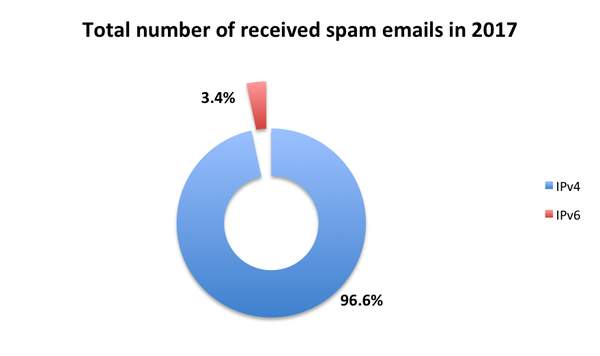 Though IPv6 is gradually replacing IPv4 on the Internet's network layer, email is lagging behind, the difficulty in blocking spam sent over IPv6 cited as a reason not to move. But would we really have such a hard time blocking spam sent over IPv6?
Though IPv6 is gradually replacing IPv4 on the Internet's network layer, email is lagging behind, the difficulty in blocking spam sent over IPv6 cited as a reason not to move. But would we really have such a hard time blocking spam sent over IPv6?
Posted by Martijn Grooten on Jun 13, 2018
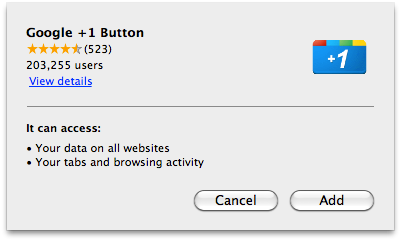 Google has made a subtle change to its Chrome browser, banning the inline installation of new extensions, thus making it harder for malware authors to trick users into unwittingly installing malicious extensions.
Google has made a subtle change to its Chrome browser, banning the inline installation of new extensions, thus making it harder for malware authors to trick users into unwittingly installing malicious extensions.
Posted by Martijn Grooten on Jun 11, 2018
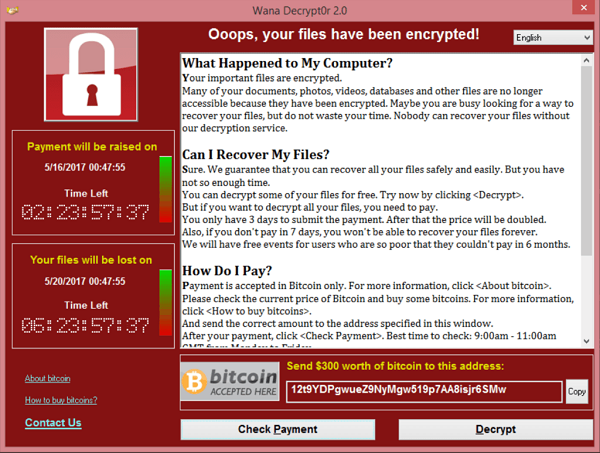 We publish a paper by researchers from Quick Heal Security Labs in India, who study the EternalBlue and DoublePulsar exploits in full detail.
We publish a paper by researchers from Quick Heal Security Labs in India, who study the EternalBlue and DoublePulsar exploits in full detail.
Posted by Virus Bulletin on Jun 1, 2018
 Several VB2018 papers deal explicitly or implicitly with threats that have been attributed to North Korean actors.
Several VB2018 papers deal explicitly or implicitly with threats that have been attributed to North Korean actors.
Posted by Martijn Grooten on May 31, 2018
 The domain of the little-used SpamCannibal DNS blacklist had expired, resulting in it effectively listing every single IP address.
The domain of the little-used SpamCannibal DNS blacklist had expired, resulting in it effectively listing every single IP address.
Posted by Martijn Grooten on May 30, 2018
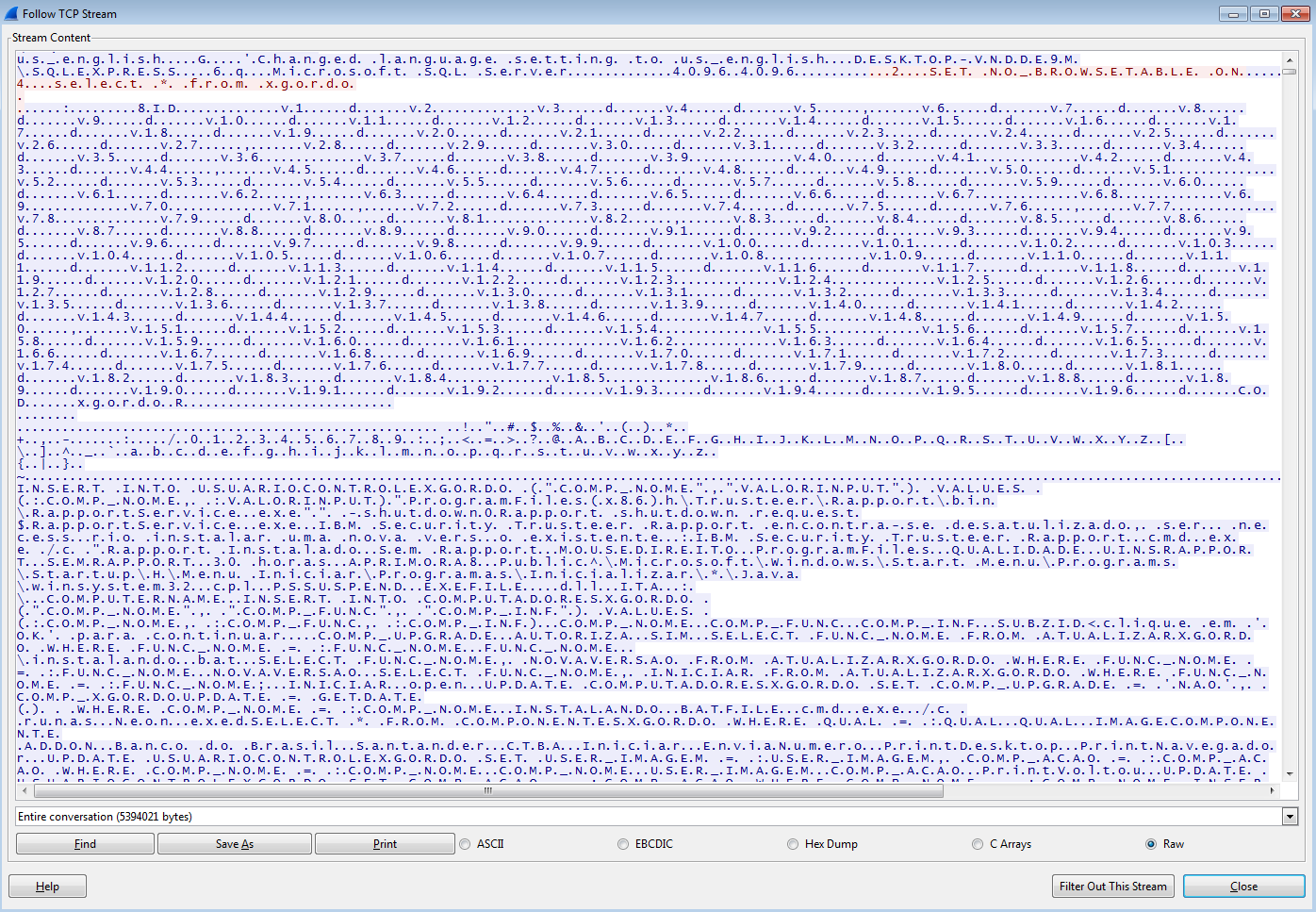 Researchers at IBM X-Force have discovered MnuBot, a banking trojan targeting users in Brazil, which is noteworthy for using SQL Server for command and control communication.
Researchers at IBM X-Force have discovered MnuBot, a banking trojan targeting users in Brazil, which is noteworthy for using SQL Server for command and control communication.
Posted by Martijn Grooten on May 24, 2018
 The 68-byte EICAR test file plays as important a role today as it did 19 years ago. In this week's Throwback Thursday we look back at a VB99 conference paper in which Randy Abrams described how this 'miracle tool' worked and how it could be used.
The 68-byte EICAR test file plays as important a role today as it did 19 years ago. In this week's Throwback Thursday we look back at a VB99 conference paper in which Randy Abrams described how this 'miracle tool' worked and how it could be used.
Posted by Martijn Grooten on May 23, 2018
 A new piece of cryptocurrency-mining malware on macOS has been found to use the popular XMRig miner.
A new piece of cryptocurrency-mining malware on macOS has been found to use the popular XMRig miner.
Posted by Martijn Grooten on May 22, 2018
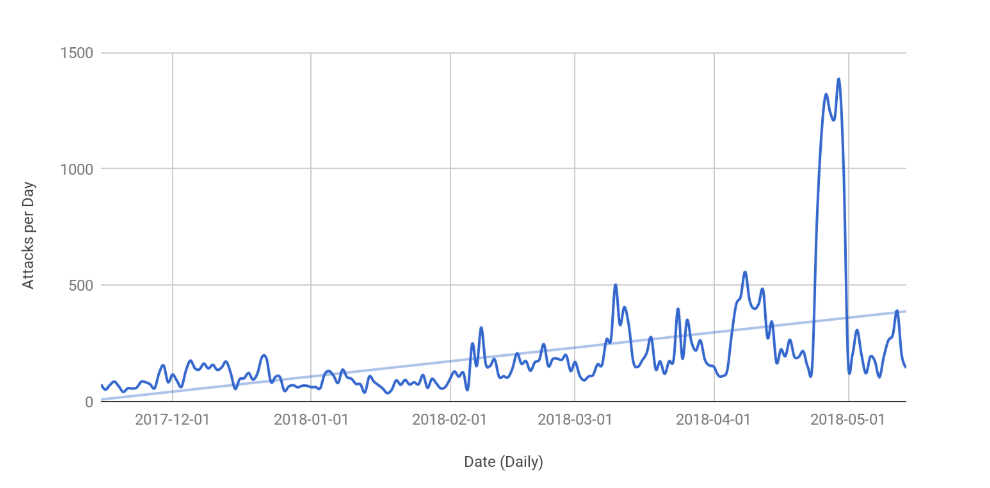 CDN provider Cloudflare reports an increase in DDoS attacks targeting layer 7 and focusing on exhausting server resources rather than sending large volumes of data. This fits in a wider trend.
CDN provider Cloudflare reports an increase in DDoS attacks targeting layer 7 and focusing on exhausting server resources rather than sending large volumes of data. This fits in a wider trend.